No products in the cart.

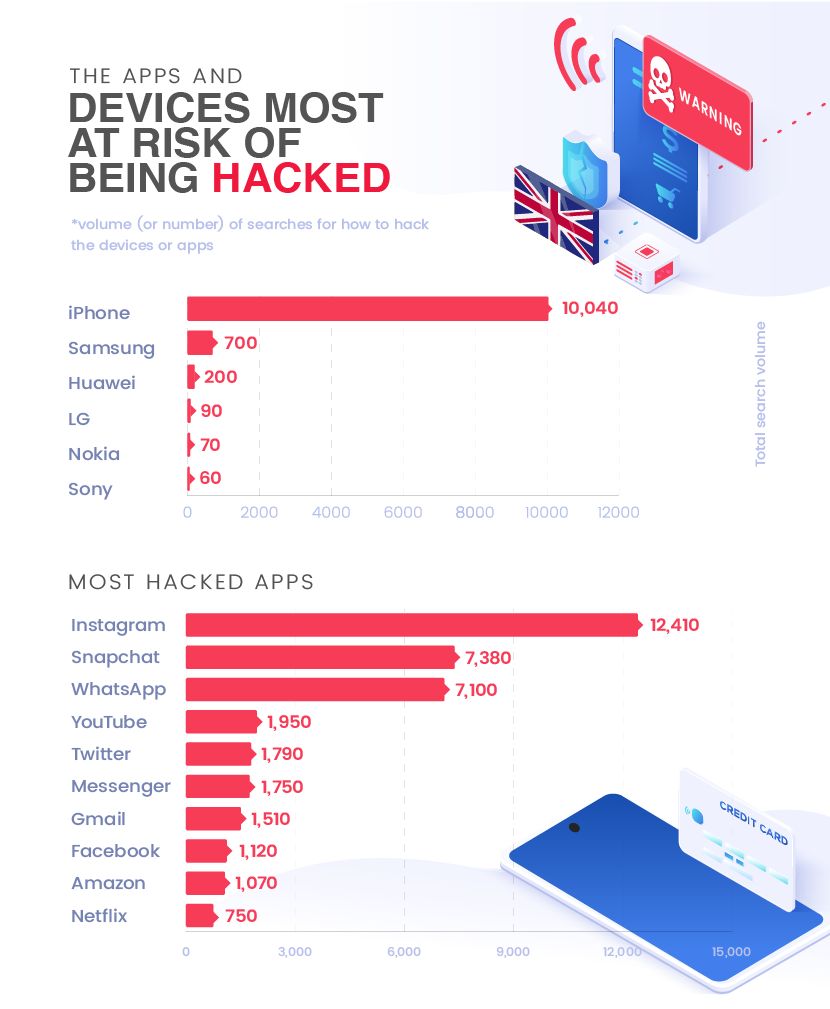
- iPhone owners are 192 times more at risk to being targeted by hackers than other phone brands.
- Over 48,010 Americans are searching information on how to hack an iPhone monthly.
- Over 10,040 Brits are searching information on how to hack an iPhone monthly.
- Sony, Nokia, LG and Huawei are the safest phones to have.
- Your Instagram account is 24 times more likely to be a target for hackers than your Netflix account.
- 66,960 Americans are interested in finding out how to hack someone’s Instagram account every month.
- Snapchat and WhatsApp accounts are not safe either, with over 35,000 Americans intending to find information on how to hack into these apps every month.
Mobile app hacking is on the rise, and a recent report from the RSA puts smartphones at the top of the list as the main channel for hackers. With that in mind, the experts with an interest in mobile technology from Case24 sought to investigate which apps are more prone to getting hacked. Simultaneously, Case 24 also had a look at the mobile phone brands that are most likely to be targeted by hackers in the US and UK.
The data was gathered by analysing monthly Google search volumes to see how many Americans and Brits are looking to find information on how to hack different apps or phone brands.
You are 192 times more at risk to get hacked if you have THIS phone
When investigating the number of times people searched how to hack different phone brands, the results show a whopping difference between the brand in first place and the other brands. In fact, the results show the following for US:
| Most hacked phone brands (US) | Total search volume |
| iPhone | 48,010 |
| Samsung | 3,100 |
| LG | 670 |
| Sony | 320 |
| Nokia | 260 |
| Huawei | 250 |
If you are an iPhone owner, then you are approximately 192 times more likely to have your phone hacked than if you were a Huawei owner.
In second place are Samsung owners, with 3,100 Americans monthly searching how to hack into their phones. LG is third with 670 searches/month, while Sony, Nokia and Huawei were the phones hackers are least interested in, with under 500 searches/month each.
The date for UK shows the following:
| Most hacked phone brands (UK) | Total search volume |
| iPhone | 10,040 |
| Samsung | 700 |
| Huawei | 200 |
| LG | 90 |
| Nokia | 70 |
| Sony | 60 |
If you are an iPhone owner, then you are 167 times more at risk to have your phone hacked than if you were a Sony owner.
In second place are Samsung owners, with 700 Brits monthly searching how to hack into their phones. Huawei is third with 200 searches/month, while LG, Nokia and Sony were the phones hackers are least interested in, with under 100 searches/month each.
What apps are most at risk of being hacked in the US?
Just like with phone brands, some apps are more prone to being hacked than others. In fact, your Instagram account is approximately 24 times more at risk of being hacked than your Netflix account. The results show that a shocking 66,960 Americans are interested in finding out how to hack someone’s Instagram account every month. Your Snapchat and WhatsApp accounts are not safe either, with over 35,000 Americans intending to find information on how to hack into these apps every month.
| Most hacked apps (US) | Total search volume |
| 66,960 | |
| Snapchat | 57,740 |
| 36,980 | |
| YouTube | 13,710 |
| 13,350 | |
| Messenger | 10,350 |
| Gmail | 7,080 |
| 5,980 | |
| Amazon | 3,460 |
| Netflix | 2,790 |
What are the apps most at risk of being hacked in UK?
For Brits, your Instagram account is approximately 17 times more likely to be targeted by hackers than your Netflix account. The results show that a shocking 12,410 Brits are interested in finding out how to hack someone’s Instagram account every month. When it comes to Snapchat and WhatsApp, over 7,000 Brits intend to find information on how to hack into these apps every month.
| Most hacked apps (UK) | Total search volume |
| 12,410 | |
| Snapchat | 7,380 |
| 7,100 | |
| YouTube | 1,950 |
| 1,790 | |
| Messenger | 1,750 |
| Gmail | 1,510 |
| 1,120 | |
| Amazon | 1,070 |
| Netflix | 750 |
Press release written by Case24
HIRE A HACKER (WEB BAILIFF CONTRACTOR) TO CHANGE YOUR SCHOOL GRADES Web Bailiff Contractor is your trusty sidekick in the battle of academic chaos. With just a few clicks, you can track your grades effortlessly, leaving you more time to tackle that monster of a term paper or binge on some well-deserved snacks. This magical tool not only simplifies the process of accessing your grades but also ensures your data is guarded like a dragon hoarding its treasure. With features like encrypted connections and real-time updates, Web Bailiff Contractor is here to make your academic journey a breeze. In the… Read more »
After losing my 2.06 BTC in 2020, I thought that was it. I mean, there are hardly any cases of successful recoveries. But fast-forward to 2022-2024, it hit its ultimate boom and I instantly knew I was not ready to give up on my bitcoin. So, I started researching known and well-rated hackers on the internet. Also trimmed them down by removing those in the red-police notice for not being legit hackers (scammers too). One DECODE HACKERS stood on top of my list. I had to trust my gut and dig deep with this one. So, I hit them up… Read more »
A team of specialists more adept than a magician with a wand is required to navigate the perilous waters of difficult recovery cases. To help you overcome the most difficult obstacles and guarantee that your misplaced Bitcoin assets return home, Brunoe Quick Hack Crypto recovery service offers their experience. As the Bitcoin space develops more quickly than a Website;”Brunoequickhack.com can learn new spells, and innovative solutions appear to strengthen asset protection. By incorporating these advancements, Brunoe Quick Hack Crypto recovery service remains ahead of the curve and offers a more durable shield than dragon scales. Like a vigilant Brunoe Quick… Read more »
Seven years in marriage not once had I ever gone out of wedlock. I always respected my vows no matter the situation. I started noticing some changes in my wifes behaviour, she started being over protective on her phone. I used to know her phone plus social media passwords but she changed all of them. As a matter of fact she kept passwords on all her communication apps, night calls started being frequent. Every time I asked she would just turn the topic to me being insecure and i don’t trust her. Naturally I’m a guy of short words, i don’t like arguments especially… Read more »
When I found out about my fiancé’s deceit, I was devastated. The daniel meuli web reocvery was recommended to me by a family member, and it turned out to be a lifeline in unraveling the truth. With its help, I delved into my fiancé’s social media accounts, including Facebook, Instagram, and Twitter, uncovering a treasure trove of evidence that shattered the facade of the life he had presented to me. The tool combed through his Facebook profile, revealing messages, comments, and interactions that painted a damning picture of his deception. Among the notifications was a message addressed to him as… Read more »
So, you find yourself in a situation that no one wants to be in – suspecting your partner of cheating. It starts with little things – missed calls, secretive text messages, and sudden changes in behavior. The doubts start to creep in, and before you know it, you’re knee-deep in suspicion. You can’t help but wonder if there’s something going on behind your back. Even though suspicions can be quite strong, you should never accuse someone without hard proof. Nobody wants to ruin a relationship over speculative thoughts, after all. That’s why having proof becomes essential. You’re looking for something… Read more »
An <a href=”https://stresserhub.org/” title=”ip stresser” target=”_blank”>ip stresser</a> is a tool designed to test a network or server for robustness. The administrator may run a stress test in order to determine whether the existing resources (bandwidth, CPU, etc.) are sufficient to handle additional load.
I was suspecting my husband was cheating on me and lying about it to my face. Thanks to my friend, she connected me to this great hacker. He spied on my husband’s phone, gave me access to everything on his phone, his email conversations, text messages and phone conversations and a whole lot more. This hacker is one of the best ever, his email address is [email protected] if anyone ever needs his service. He’s reliable and efficient and you can text,call or whatsapp him on +13134033941 ,..,,
Everyday I wake, I am very glad I hired this great hacker Viktor. This man helped me hack an iPhone within 6 hours. I could read all messages on the phone, emails, access to photos/ videos and an option to listen to phone calls. I was never the kind of guy to believe in hackers but I guess I was wrong all along. IF YOU NEED A HACKER, CONTACT VIKTOR VIA EMAIL: viktorhackworld @@@@@@@ gmail. com
He offers so many other services, it’s a long list.
Hello everyone! I will like to recommend BLISS PARADOX RECOVERY to anyone out here who have been victimized my internet fraud/scams. Never say never to your all that you lost to scammers. Bliss Paradox Recovery, licensed hack experts are here to help with this type of situation. I also want to say a BIG THANKS to the team for working tirelessly to get back what I was duped. Believe me, you wouldn’t wanna miss this opportunity to get back what have been taken away from you by internet fraudsters. Help yourself so they can help you. CONTACT DETAILS: MAIL: [email protected] WHATSAPP:… Read more »
With the knowledge of phone security measures, Wizard Web Recovery utilizes advanced techniques to bypass these obstacles. While the specifics remain a mystery, the service is capable of accessing the phone’s data without alerting the user. It’s like having a secret agent silently working behind the scenes to retrieve the truth. Through this process, I was able to uncover the hidden messages, photos, and activities that confirmed my partner’s infidelity. In conclusion, wizardwebrecovery(@@@@@@@)programmer(.)net played a pivotal role in lifting the veil of uncertainty and revealing the truth about my partner’s actions. While the journey was emotionally challenging, having concrete evidence… Read more »
I invested the sum of $ 205,800 worth of Bitcoin with a cryptocurrency company I met online. After a couple of weeks, my initial investment had increased from $ 205,800 to $ 392,650. This felt so good as the investment grew rapidly in just a few weeks. When it was time to retire, my withdrawal request was denied, all effort to make withdrawal declined, then I realized I had been ripped off.
Thanks to ([email protected] ) website: https://centurycyberhacker.pro/ or Telegram : @Marvels109 they help me recover all my stolen funds back am so grateful
If you have lost your funds to any crypto currency investment scam or to any type of scam and you need to retrieve
your money back then you should contact > recoverfunds.investigator247 @@@@@@@ gmail .. com, When i thought i lost my life savings to a crypto currency scam i invested into, i lost hope until i was referred to this recover investigator. You can also contact him if you have lost funds to any scammer.
Get a private hacker to help hack whatsapp, facebook , snapchat, instagram, mobile phones or change school grades.
He has helped i and my friends with different jobs like changing our school grades without any trace and hacking
into my boyfriends mobile phone .If you also need this type of service then i suggest you send a message to this
professional hacker : [email protected]
nice
Private Hacker is the only professional hacker i have seen on here that will deliver 100%. After loosing some funds to some amateur hackers that could not hack into a mobile phone , I decided to try another hacker and he got me access into my ex partners mobile phone remotely and i saw a lot of things that made me file for a divorce .
Guys its best to always know what your partner is up to and thinks about you. You can also reach him on this email address PRIVATEHACKER247 @@@@@@@ GMAIL DOT COM.
I appreciate you getting this done to me so quickly. Thanks for your help.
I got access to my husband iPhone i got all his text messages, call details, WhatsApp details, Facebook messenger. I’m so sad he is cheating on me. I’m sending all evidence to my lawyer. that will used in court against him. contact: (Stephenlogicalhacklord at gmailCom), or text him or WhatsApp +16025626646 he ready to help anytime contact him for your hacking jobs…….
Great service delivery. I am here to thank Ethical Hacks services and to also let people know that your services is the real deal and very reliable. I now have complete access to see and monitor all my husband’s chat messages on WeChat, i have been able to retrieve and recover all his deleted messages also, all thanks to you. This way i will get to know if he has been honest with me or not and if he is cheating on me. All this wouldn’t have been possible without your great help and assistance. text him on hackrighttech @gmail… Read more »
Excellent blog!
You did amazing job.
If you need a credit boost on all bureaus then credit Hero is the right person for the job, He increased my
credit score from a poor 537 up to 790n and removed all the negatives on my credit.
He increased my 3 credit card limits to 60k each and i now get approvedfor different loans.
credit hero has also helped my wife and some colleagues at work with their credit repair,
He is 100% genuine and reliable .
You can send him an email here > credithero123 @@@@@@@ g mail dot com
Donkey Kong who has kidnapped a woman named Pauline, and the player controls a character named Jumpman (later known as Mario) who must climb ladders and jump over obstacles to rescue her.
This SMM panel has you covered if you’re looking for a trusted way to acquire free Instagram followers. Their services guarantee the protection of your account while you increase your following because they are both efficient and secure.
I appreciate you getting this done to me so quickly. Thanks for your help.
I got access to my husband iPhone i got all his text messages, call details, WhatsApp details, Facebook messenger. I’m so sad he is cheating on me. I’m sending all evidence to my lawyer. that will used in court against him. contact: (Stephenlogicalhacklord @@@@@@@ gmailCom), or text him or WhatsApp +16025626646 he ready to help anytime contact him for your hacking jobs……
My husband didnt know i could view the activities on is phone for almost a year this was not by my power but this hacker called Tech Wizard. Because of my husbands change in behaviour i decided to search for a hacker who would help me hack into his phone, so many recommendations showed but i decided to give this particular hacker a try and he gave me a wonderful job within 24hrs. you can contact him for any hack related services from social media hacking, gmail hacking, phone hacking, call logs, text messages etc. send him a mail below:… Read more »
Do you need to spy on your partners mobile phone remotely without any trace back to you ?
you can view your partners text messages, whatsapp messages , imessage , call logs, listen to calls,
photos and videos, instagram etc. i was introduced to this private hacker who program my phone with my partners
phone when i suspected he was cheating and i was able to see conversations with a lady he was married too
and he never told me about it. guys you can send an email to > [email protected] if you need this type of service.
I was greatly convinced by a female lady on social media to invest in crypto, she directed me to a broker web where i signed up and make a deposit, i kept on adding to my capital, after my first attempt to withdraw $2k was successful not knowing it was programmed cause the lady advise me to withdraw 2k. by the time i realized i have been scammed the sum of $198,750 and this money was all i had and i have worked so hard to save this money, it was like the world has turned against me i tried… Read more »
Yes it is very possible that a good hacker can hack into a cellphone and grant you access to all the messages on the phone. I hired one and he delivered perfectly well. He helped me gain access to my ex’s text messages, WhatsApp messages, Facebook and Instagram. He also helped me recover deleted messages. His name is Albert. IF YOU NEED HELP, CONTACT HIM ON HIS EMAIL: Vadimwebhack@@@@@@@ gmail. com
He offers many other services like removing bad records, credit repair/ score boost and many other services I can’t mention them all.
THE BEST HACKER / WIZARD LARRY Upgrade credit score, fix Facebook, Instagram, WhatsApp, and other social media hacks. Fix any investment platform. Recover from any fraud. Hack CashApp. Fix any dating scam. Upgrade school results. Track your spouse in real time. Have you ever felt the urge to trade binary options? Have you have a negative encounter? Have you ever been duped? Scams involving binary options trading and binary option loss recovery are fairly common. They are the greatest, so get in touch with them by email and WhatsApp and visit their website. You’ll thank me later. Email address: (wizardlarry@mail. com).… Read more »
I joined channels and associated web applications that are manipulating users into joining The fraud operation appears to be promoting a USDT (also known as Tether) cryptocurrency investment scheme. USDT, which is pegged to the US Dollar and known as a stablecoin, has itself been heavily criticised over its opaque practices, and has been the subject of multiple regulatory and legal probes. long story cut short I got entangled I paid 37,000k pounds even when I try to withdraw they pinned it to taxes I knew all this and how they operate after I contacted a group of expertises COREASSETINC whom… Read more »
Every time I did log on to the trading platform I was using, it looked like I was reaping windfall profits. in fact, I was one of a growing number of people who’ve fallen victim to cryptocurrency scams. I heard, and I read, but somehow I thought that I am not going to be one of them turned to cryptocurrency investments after the pandemic upended my life. I run a business selling equipment and supplies to restaurants in the Los Angeles area. But many of them shut their doors when lockdown orders went into effect. I lost a lot of clients… Read more »
Today’s digital age, cryptocurrencies have gained immense popularity, attracting both seasoned investors and newcomers alike. Unfortunately, this surge in interest has also led to an increase in online scams targeting unsuspecting individuals. I will share my personal experience of being scammed online with crypto and how I recovered some of it from a hacker @@@@@@@Darkrecoveryhacks on telegram .Like many others, I was captivated by the potential of cryptocurrencies to revolutionize the financial world. The promise of high returns and the allure of being part groundbreaking technology were too enticing to resist. Eager to dip my toes into the crypto market,… Read more »
As a project manager, I had tried to invest using a platform , a cryptocurrency platform founded by the influential . The platform was plagued by technical problems, and I found myself unable to make swaps after depositing funds. I got error message after error message. I kept reporting the issue, and customer service representatives told me a solution was in the works. Then in April of 2022, announced that the platform would be shutting down all operations that June. I did as the platform advised and immediately started trying to withdraw my funds. But I would never see that money… Read more »
During the beginning of the COVID pandemic, my husband, who had been battling illnesses for years, passed away. As a former nurse, I turned to the internet in search of others who were experiencing a similar grief. Unfortunately, what I found were predators. They targeted me because they knew I had some financial means due to my background as a nurse. Losing my husband was incredibly difficult for me, and it took a toll on me emotionally. I became trapped in a web of cyber-relationships where requests for money started pouring in. They asked for thousands of dollars to cover… Read more »
HOW CAN I RECOVER MY LOST CRYPTO ? CRYPTO SCAM VICTIMS RECOVER THEIR LOST FUNDS THROUGH LOST RECOVERY MASTERS.
The Lost Recovery Masters is a team of experienced Crypto Experts currently collecting funds back to all scam victims. Anyone that has fallen prey to these fake online imposters and bogus investments Schemes contact Lost Recovery Masters and explain your situation; They will assist you in all crypto scam retrieval funds, bitcoin wallets reclaiming, investment scam, mobile mass surveillance, and cyber – attacks.
Support team Mail: ([email protected])
WhatsApp: +1(204)819-5505.
Web; https://lostrecoverymasters.com/
Don’t forget to mention Michelle Brice referred you.
I’ve heard alot of stories and read many article of people loosing their hard earned money to scammers online who at first pretend to be sweet and friendly in the beginning but with the intention of sending you out on to the streets. I never hoped nor wished to be here telling you all my ordeal in the hands of these scammers and how the whole situation turned out to be. I lost a total of $540,000k to a binary investment scheme on instagram, my whole life flashed before my eyes when my account on the said platform restricted my… Read more »
Do you need a hacker? Do you need to access your partner’s email to keep track of him? As a parent, would you like to know what your kids are doing on social media everyday college grades change, (including Facebook, Twitter, Instagram, WhatsApp, WeChat and other things to make sure you don’t have problems? Banking, Cash Flow, Criminal dossier, DMV) Tax, call him and he’ll do the job. He is a professional hacker with years of experience. Write to him through hackrighttech @gmail com.
I remember in 2021, my credit score was horrible, I had so many collection accounts and would not approve for anything. I had rental debt, charge offs, student loans, tax liens e.t.c. from your credit report.
I was then introduced to [email protected] by Mr. Fred who happened to be my old time friend and my credit score went from 527 to 800 within few days and I was able to get a home loan and eligible for several credit cards. I can always recommend CREDIT HERO to anyone who desires to have a better credit life.
Even though spying or hacking someone’s phone might be illegal, the situation surrounding my marriage warranted it. However, despite several attempts, getting a reliable hacker proved to be a herculean task till I was introduced to hackerspytech AT G m ail c om . In fact, I have been scammed many times in my attempts to hire a professional hacker. Here is the problem, I suspect my husband is seeing other ladies. Most of the hackers I contacted collected my money and I never heard from them. I decided to try for one last time before I finally give up.… Read more »
I recently found out that you could boost your poor credit by using an online credit expert. Few months back I tried to request a loan to buy a house for my new family but i got denied due to my bad credit. My loan officer referred me to this credit repair guru { credithero123 at g mail . com } , I sent him a message and got a swift response . He expunged all the negatives messing my credit up permanently in a month and increased my credit score to 790. After he added good trade lines I requested… Read more »
Get in touch with Spyhackpro9 for all
your hack related such as; Cloning,
Tracking, Spying, Retrieving of deleted
text messages, Upgrading of results,
Hack social media accounts, Erase
criminal record. His service is safe and
secure. Get in touch with him via his email
spyhackpro9 AT G m ail C o m
i won the lottery and then people kept on asking me how did i do it, well yea there is a little secrete you all never knew about, i was able to win the 80.000.000 lottery with the help of Dr Dominion lottery winning spell, he gave me number to play and instructed me when to play the lottery and i did as he instructed, my dear friends getting rich is never by luck it’s something we all have to work for, people have been playing same lottery for years now and have never won, we need to be on… Read more »
People cheats due to lack of being contented with their partner or some other reasons. You can’t trust your partner 100% cause you get to know different behavior in a person each day. if you suspect your partner is cheating it’s better to know the truth at once so you can get the peace of mind before it’s too late and you live a life full of regrets. You can’t do this on your own that’s why you need the assistance of an IT expert/PI to monitor and track all the activities of your partner in one swipe. Here is… Read more »
Losing $150k to a cheap online scammers is what anyone would not like to witness, I have been put to depression for someday by an online scammers who made me to believe that I can earn up to $300k USD by investing $150k. I invested all my funds hoping to receive it back in a bigger form. I was totally disappointed and shattered when I was denied the access of withdrawing the profit nor my Capital well all thanks to a recovery hacks who helped me recover my whole funds and the profits. You can contact them now at their… Read more »
They have vast solutions to all online issues contact them through their m ail hackerspytech at g m ail c om Their services includes hacking phone,database,record expungements,spy,and private investigator .Their hacking service is completely anonymous and very easy to use. The most interesting thing about this is, it is very fast and comes with lots of features
Thanks to Allen@alienwizbot .com for hacking services rendered to me. the service was satisfactory and in terms of use it’s very understanding and easy to operate, best mobile spy i have ever enjoyed without any single stress.
I believe this information will be very useful to someone out there. I have been looking for a way to spy on my husband’s phone for quite some time but sadly most of the information available has not been useful. Tried some apps and softwares and none worked. I found this page some days ago but didn’t take it seriously. But the issues that needed to be resolved didn’t go away so I decided to give it a try. I contacted wizardcyberfileshacker at gmail. com for help and they came through. I now have access to my husband’s iPhone and I… Read more »
Hacking a mobile phone is usually something that requires hiring an expert to get it done for you to get your desired result. These mobile hacks actually work fine but most people have problems using it because bulk of the job is done and highly dependent on the hacker. In most cases, the only way you can get it done yourself is if you really know how to hack. Otherwise, your best bet will be to hire a professional hacker, and I recommend HACKERSPYTECH at g mail dot com I have used his services and his is highly professional, he’s… Read more »
Trust me there are a lot of things a good hacker can help you achieve. I never imagined it was nearly possible that someone could move my credit score from 520 to 860 within 5 working days. Trust me I contacted this hacker Albert Vadim reluctantly because I had ran out of options. Within 5 days my life literally changed. I was granted loan, I moved my family to a beautiful house, I am grateful. IF YOU NEED HELP, CONTACT ALBERT VADIM VIA EMAIL: Vadimwebhack AT gmail. com Just a few days back, he helped a friend of mine based… Read more »
Because someone searches the internet for the Anarchist’ Cookbook online does not mean they actually find it and manage to follow the instructions. I frequently try to find something on Ebay and Amazon and come uo empty handed for what I was looking for. Congratulations. You mayly have the most mindnumbingly dumb and horribly thought out article ever. You still have a job after this one?
search for info does not always mean they want to hack it.