No products in the cart.
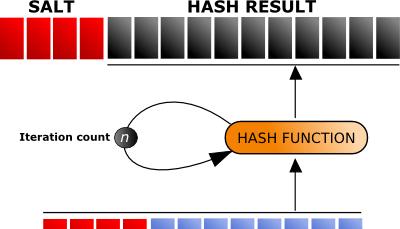
Many applications, operating systems, and other authentication mechanisms that take in credentials utilize a known defense against cyber-attackers known as "salting." For the non-IT or InfoSec professionals, whenever you create an account for any service, you more than likely created a password. Even though this is a known defense, it's got different methods of implementation. The problem is, depending on this method of implementation, modern computing power makes it still a very low barrier to entry in "cracking" your passwords if the service you're using is ever compromised. After a debate with another Information Security colleague and with a developer asking me what would be a "better practice" of implementing credential salts, I've decided to make this article and demonstration. Hashing Many developers of applications and systems have taken your password that you have entered and sent it through a mathematical function that turns your password into an encoded....
A great hacker is really worthy of good recommendation , Henry
really help to get all the evidence i needed against my husband and
and i was able to confront him with this details from this great hacker
to get an amazing service done with the help ,he is good with what he does and the charges are affordable, I think all I owe him is publicity for a great work done via, Henryclarkethicalhacker at g mail com, and you can text, call him on whatsapp him on +12014305865, or +17736092741,