No products in the cart.
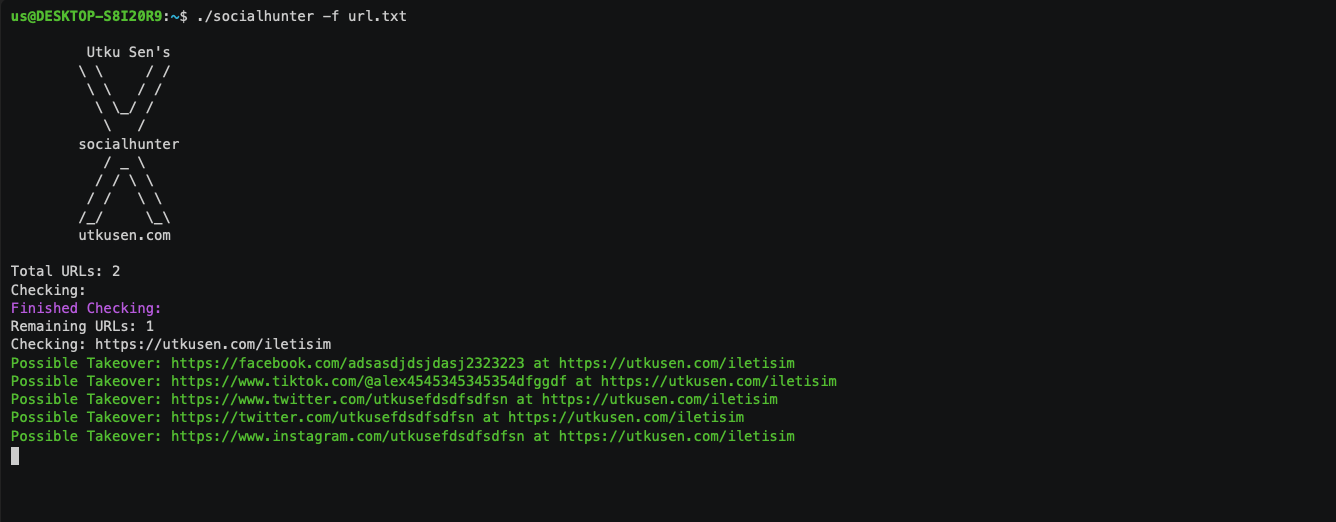
Crawls the given URL and finds broken social media links that can be hijacked. Broken social links may allow an attacker to conduct phishing attacks. It also can cost a loss of the company's reputation. Broken social media hijack issues are usually accepted on the bug bounty programs. Currently, it supports Twitter, Facebook, Instagram and Tiktok without any API keys. More at: https://github.com/utkusen/socialhunter DEMO Installation From Binary You can download the pre-built binaries from the releases page and run. For example: wget https://github.com/utkusen/socialhunter/releases/download/v0.1.1/socialhunter_0.1.1_Linux_amd64.tar.gz tar xzvf socialhunter_0.1.1_Linux_amd64.tar.gz ./socialhunter --help From Source Install Go on your system Run: go get -u github.com/utkusen/socialhunter Usage socialhunter requires 2 parameters to run: -f : Path of the text file that contains URLs line by line. The crawl function is path-aware. For example, if the URL is, it only crawls the pages under /blog the path -w : The number of workers to run (e.g -w 10).....
A very big thanks to kelvinethicalhacker at gmail com for the great the work you done for me, i got the email address on the net web when i needed to hack my husband cell phone he helped me within few hours with whatsApp hacking and GPS location tracking direct from my person phone i know how my husband walks, thanks for the helped you do for me for every grateful for your helped, you can contact him through gmail via kelvinethicalhacker at gmail.com or Telegram, calls, text, number +1(341)465-4599, if you are in needed of hacking services, contact him..
A great hacker is really worthy of good recommendation , Henry
really help to get all the evidence i needed against my husband and
and i was able to confront him with this details from this great hacker
to get an amazing service done with the help ,he is good with what he does and the charges are affordable, I think all I owe him is publicity for a great work done via, Henryclarkethicalhacker at gmail com, and you can text, call him on whatsapp him on +12014305865, or +17736092741,