No products in the cart.

The SQRL, or Secure Quick Response Login, a QR-code-based authentication, is an amazing system that makes our lives easier, as it allows us to quickly sign into a website without having to memorize or type in any username or password. Sounds great, right? Any website that implements QR-code-based authentication system will display a QR code (for example, on a computer screen) and all you have to do is just scan that code with a mobile phone app and you can log-in. You don’t even need to remember your username or password, everything is in the code.
The QR codes are considered secure, because they randomly generate a secret code, which is never revealed to anybody else. It is very important, especially since passwords can be stolen by using a keylogger, a man-in-the-middle (MitM) attack, or even a brute force attack.
Unfortunately, it’s not as safe as it sounds.
Egyptian Information security researcher and Cyber Security Advisor at Seekurity Inc. Mohamed A. Baset and his team has come up with a proof-of-concept demonstrating a new session hijacking technique that can be used to hack accounts from services that use the "Login with QR code" feature as a secure way to login to accounts.
What exactly is QRLJacking?
As we can read on the github page: “It is a simple social engineering attack vector capable of session hijacking affecting all applications that rely on “Login with QR code” feature as a secure way to log into accounts. In a simple way, in a nutshell victim scans the attacker’s QR code results of session hijacking.”
What do you need to perform QRLJacking?
QRLJacking is a technique based on simple solutions. So to carry out a successful attack, you need only two things: QR Code Refreshing Script and well crafted phishing webpage.
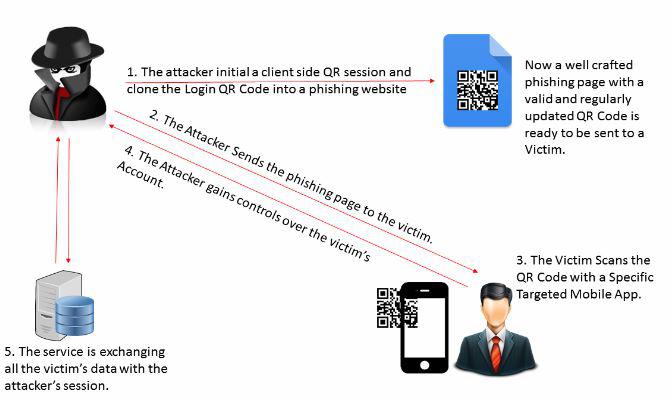
Now that we know the basics let's see how QRLJacking attack works. The team responsible for creation of this attack presents a small visualization:
- The attacker initializes a client side QR session and clones the Login QR Code into a phishing page
- The attacker sends the phishing page to the victim.
- Potential victim scans the QR Code with a specific targeted Mobile App.
- When the authentication process is completed, the attacker gains control over the victim's account.
- Then the service starts exchanging all the victim's data with the attacker's browser session.
Here is a demonstration video of using QRLJacking
How do you protect yourself against this?
Luckily, Mohamed’s team prepared a list of recommendations for users that would like to prevent those attacks. The most drastic solution is to stop using Login with QR code. It will definitely protect your accounts and data but I would consider this option as a final resort. Another method requires restricting any authentication process based on different locations. Also IP restriction will improve your security.
For more information about QRLJacking check OWASP and Github. We also recommend visiting Mohamed’s YouTube channel where you can watch more video demonstration of QRLJacking.
A great hacker is really worthy of good recommendation , Henry
really help to get all the evidence i needed against my husband and
and i was able to confront him with this details from this great hacker
to get an amazing service done with the help ,he is good with what he does and the charges are affordable, I think all I owe him is publicity for a great work done via, Henryclarkethicalhacker at g mail com, and you can text, call him on whatsapp him on +12014305865, or +17736092741,
After victim scan the QR, then attacker got WhatsApp session. Ehat happen to the victim WhatsApp did it got log out or what.