No products in the cart.
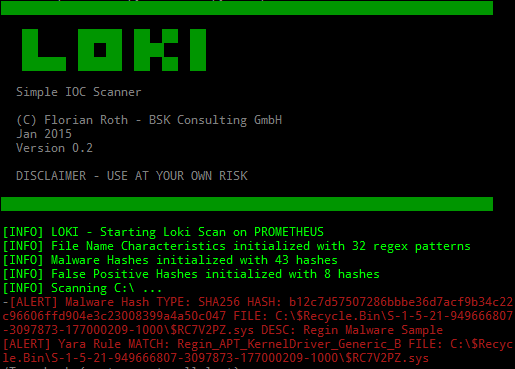
Scanner for Simple Indicators of Compromise - https://github.com/Neo23x0/Loki Detection is based on four detection methods: 1. File Name IOC Regex match on full file path/name 2. Yara Rule Check Yara signature match on file data and process memory 3. Hash Check Compares known malicious hashes (MD5, SHA1, SHA256) with scanned files 4. C2 Back Connect Check Compares process connection endpoints with C2 IOCs (new since version v.10) Additional Checks: 1. Regin filesystem check (via --reginfs) 2. Process anomaly check (based on [Sysforensics](https://goo.gl/P99QZQ) 3. SWF decompressed scan (new since version v0.8) 4. SAM dump check The Windows binary is compiled with PyInstaller and should run as x86 application on both x86 and x64 based systems. How-To Run LOKI and Analyse the Reports Run Download the newest version of LOKI from the releases section Extract the program package Run loki-upgrader.exe on the system with Internet access to retrieve the newest signatures Bring....
A very big thanks to kelvinethicalhacker at gmail com for the great the work you done for me, i got the email address on the net web when i needed to hack my husband cell phone he helped me within few hours with whatsApp hacking and GPS location tracking direct from my person phone i know how my husband walks, thanks for the helped you do for me for every grateful for your helped, you can contact him through gmail via kelvinethicalhacker at gmail.com or Telegram, calls, text, number +1(341)465-4599, if you are in needed of hacking services, contact him..
A great hacker is really worthy of good recommendation , Henry
really help to get all the evidence i needed against my husband and
and i was able to confront him with this details from this great hacker
to get an amazing service done with the help ,he is good with what he does and the charges are affordable, I think all I owe him is publicity for a great work done via, Henryclarkethicalhacker at gmail com, and you can text, call him on whatsapp him on +12014305865, or +17736092741,