No products in the cart.
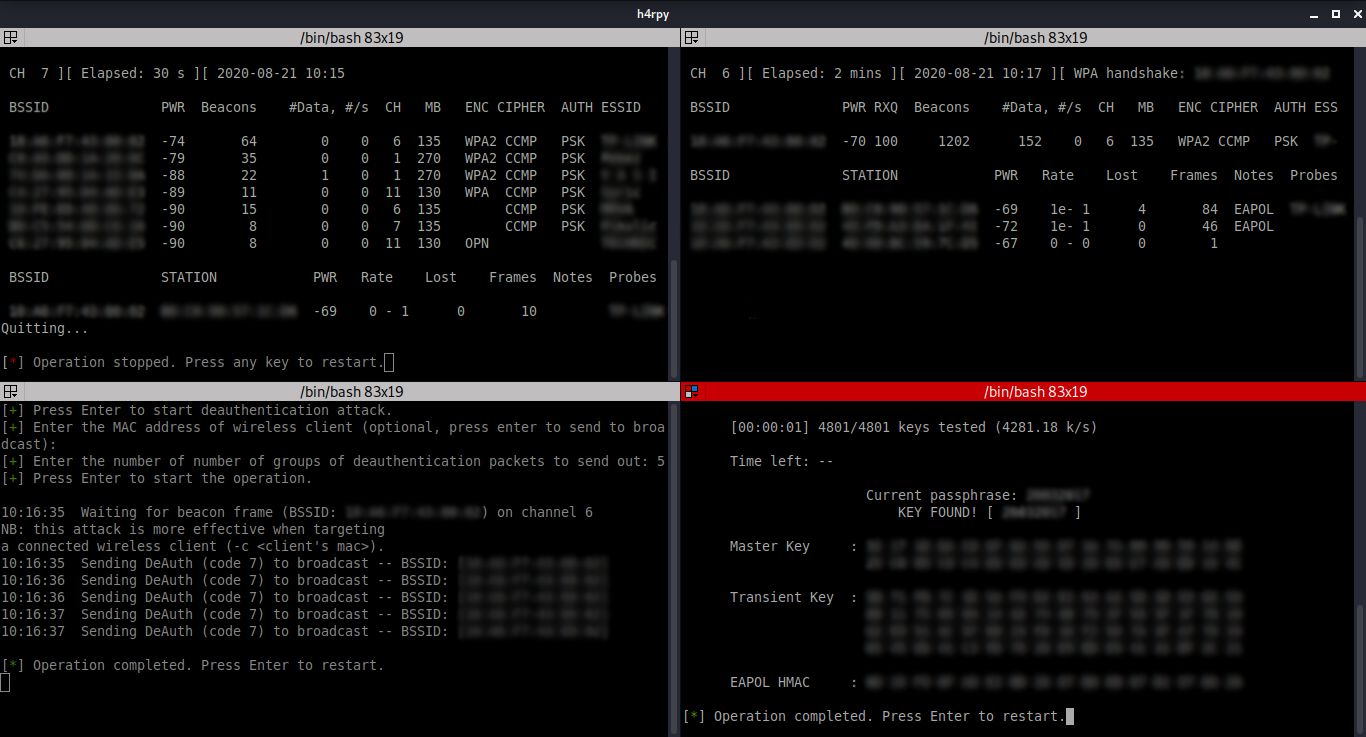
h4rpy provides a clean interface for automated cracking of WPA/WPA2 PSK networks. h4rpy enables monitor mode on a selected wireless interface, scans the wireless space for access points, tries to capture WPA/WPA2 4-way handshake for the access point, and starts a dictionary attack on the handshake. It is also possible to send disassociate packets to clients associated with the access point. Installation: The installation consists of cloning the repo, running a script that will install dependencies (aircrack-ng framework and Terminator are required in order to run h4rpy), and making h4rpy executable. The script only works with an apt package manager (Debian based distributions). # git clone https://github.com/MS-WEB-BN/h4rpy/ # cd h4rpy # sudo bash config.sh # sudo chmod +x h4rpy Usage: To run h4rpy: # sudo ./h4rpy Top-left: Enabling monitor mode, scanning for access points (packet capturing of raw 802.11 frames); Top-right: Packet capturing on selected wireless network, capturing the WPA/WPA2....
Subscribe
0 Comments