No products in the cart.
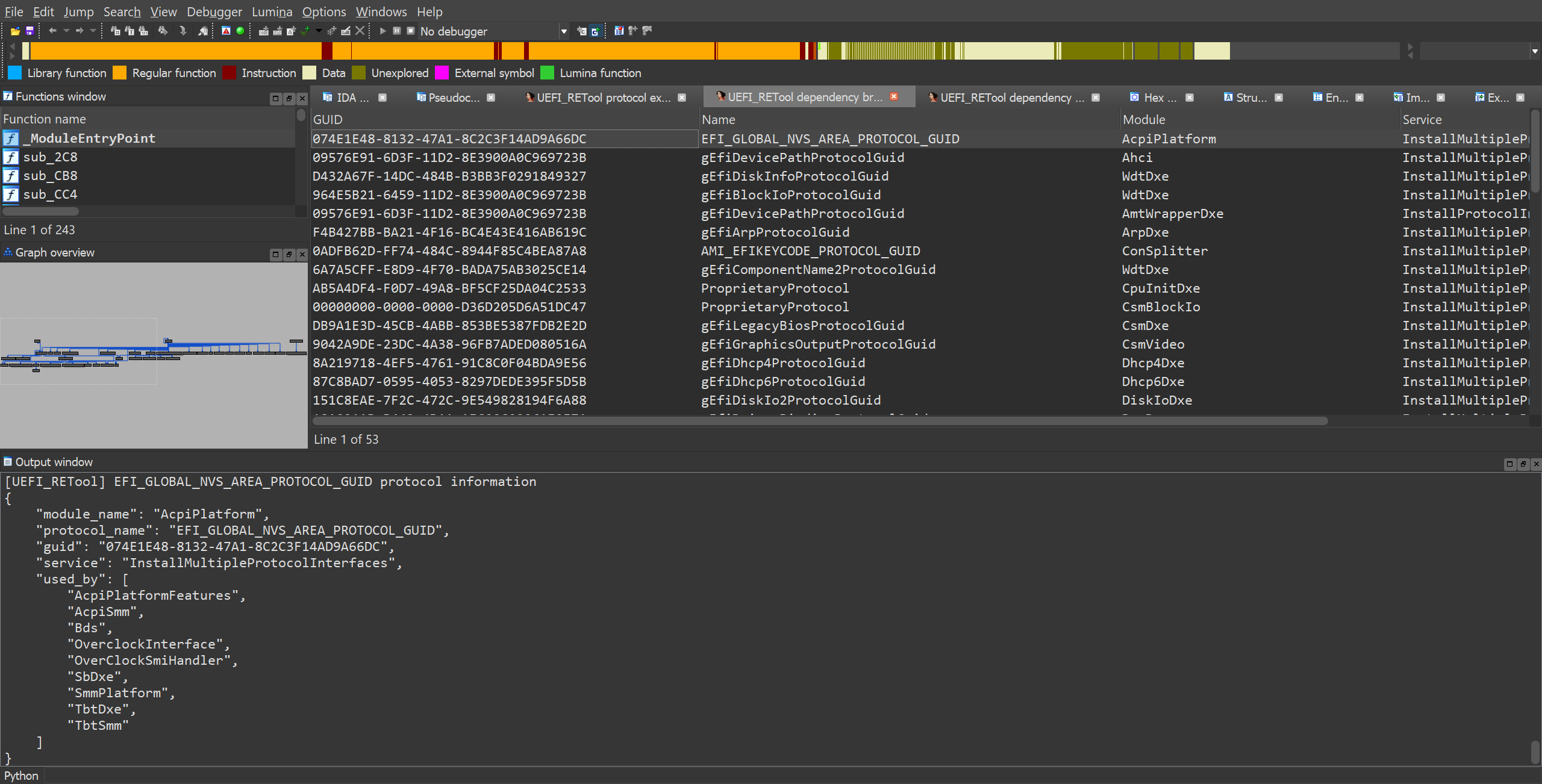
UEFI firmware analysis with uefi_retool.py script Usage: Copy ida_plugin/uefi_analyser.py script and ida_plugin/uefi_analyser directory to IDA plugins directory Edit config.json file PE_DIR is a directory that contains all executable images from the UEFI firmware DUMP_DIR is a directory that contains all components from the firmware filesystem LOGS_DIR is a directory for logs IDA_PATH and IDA64_PATH are paths to IDA Pro executable files Run pip install -r requirements.txt Run python uefi_retool.py the command to display the help message Commands python uefi_retool.py Usage: uefi_retool.py [OPTIONS] COMMAND [ARGS]... Options: --help Show this message and exit. Commands: get-images Get executable images from UEFI firmware. get-info Analyze the entire UEFI firmware. get-pp Get a list of proprietary protocols in the UEFI firmware. get-images python uefi_retool.py get-images --help Usage: uefi_retool.py get-images [OPTIONS] FIRMWARE_PATH Get executable images from UEFI firmware. Images are stored in "modules" directory. Options: --help Show this message and exit. Example: python uefi_retool.py get-images test_fw/fw-tp-x1-carbon-5th.bin get-info....
Subscribe
0 Comments