No products in the cart.
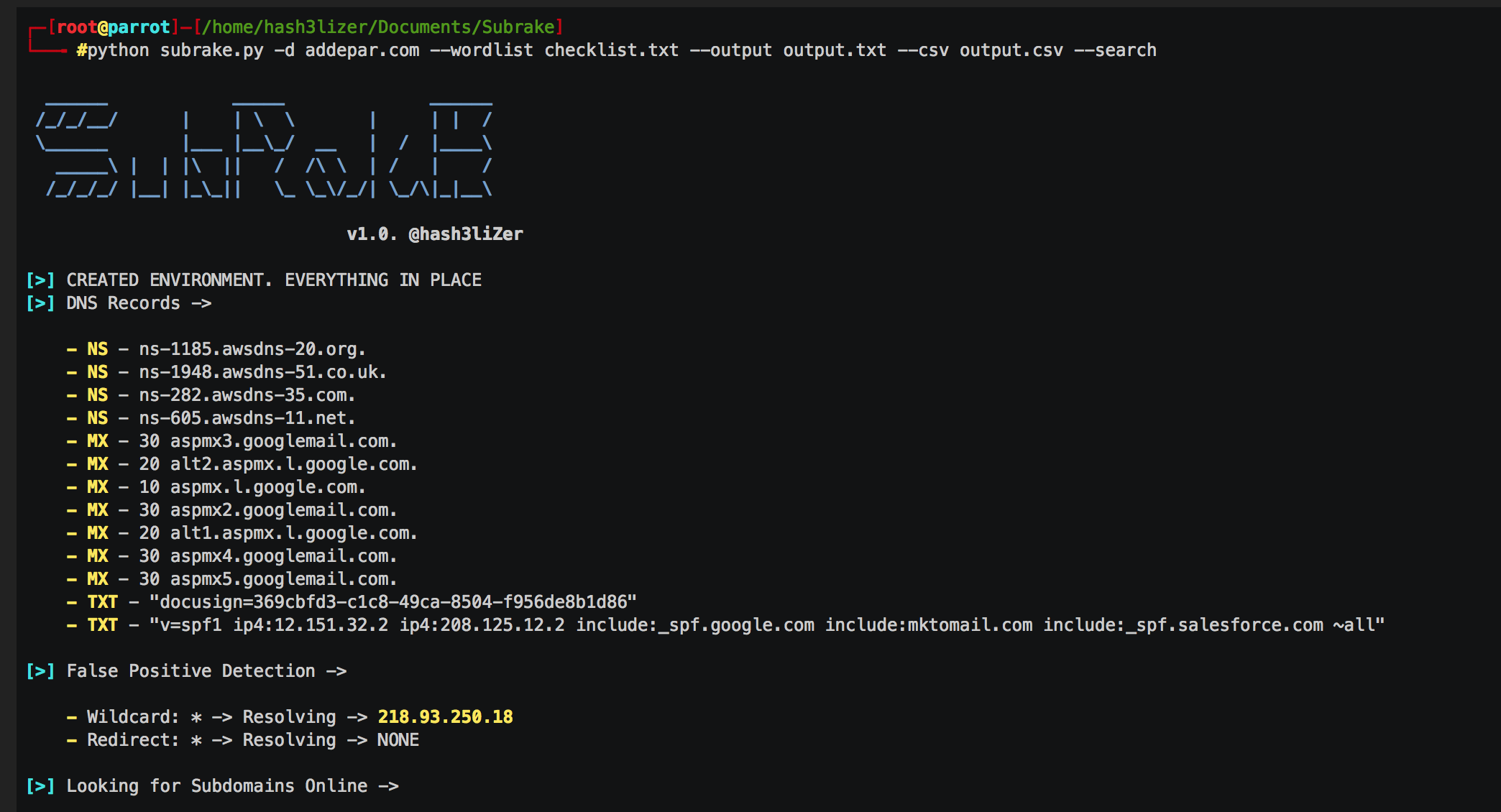
Subrake - A Powerful Subdomain Scanner & Validator Written in sockets and requests which makes it a lot more faster and easier to manage. It works by enumerating subdomains by searching them on web and by using local wordlists. It further identify the assets of a domain based on their ip and CNAME records and identify subdomains which are using the same IP addresses. It also scan ports if are given and enumerte possible server engines used on assets using the SERVER header returned in the response. It also enumerates possible returned HTTP status codes on port 80 and 443. Key Features of Subrake Use built-in low level sockets to connect subdomains and other assets Search Subdomains Online on the Web. Validate Subdomains Using associated IP address. Identify False Positives. Internal Filtering using --filter option Store data in plain text and CSV formats. Built-in Port Scanning Fitering Into More Results....
Subscribe
0 Comments