No products in the cart.
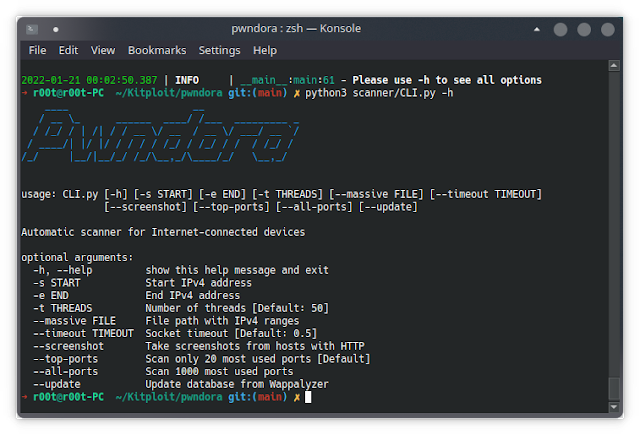
Introduction Pwndora is a massive and fast IPv4 address range scanner, integrated with multi-threading. Using sockets, it analyzes which ports are open, and collects more information about targets, each result is stored in Elasticsearch. You can integrate with Kibana to be able to visualize and manipulate data, basically it's like having your own IoT search engine at home. Features Port scanning with different options and retrieve software banner information. Detect some web technologies running on servers, using Webtech integration. Retrieves IP geolocation from Maxmind free database, updated periodically. Possibility to take screenshots from hosts with HTTP using Rendertron. Anonymous login detection on FTP servers. Send notifications with results using Slack API. Visual Getting Started Make sure you have $HOME/.local/share directory, to avoiding issues with Webtech. To use slack argument, you should configure Incoming Webhooks URL in config.py Clone this repository Install requirements with Python PIP Set password for Elasticsearch and Kibana containers in docker-compose.yml Configure connection....
Have you ever wanted to spy on your spouse’s phone or wanted to monitor their phone? you may want to know what is happening in their life or how they are communicating with someone else. or maybe you want to protect them from ex either way. you can contact ([email protected]), talk about it with kelvin. you want to hack your husband’s whatsapp account text messages on iphone or android phone remotely and provide ways of doing it without installing any software on the target device. you will get complete access to whatsapp, facebook, kik, viber, messenger, text messages and other… Read more »
A very big thanks to kelvinethicalhacker at gmail com for the great the work you done for me, i got the email address on the net web when i needed to hack my husband cell phone he helped me within few hours with whatsApp hacking and GPS location tracking direct from my person phone i know how my husband walks, thanks for the helped you do for me for every grateful for your helped, you can contact him through gmail via kelvinethicalhacker at gmail.com or Telegram, calls, text, number +1(341)465-4599, if you are in needed of hacking services, contact him.
A great hacker is really worthy of good recommendation , Henry
really help to get all the evidence i needed against my husband and
and i was able to confront him with this details from this great hacker
to get an amazing service done with the help ,he is good with what he does and the charges are affordable, I think all I owe him is publicity for a great work done via, Henryclarkethicalhacker at gmail com, and you can text, call him on whatsapp him on +12014305865, or +17736092741,
image in blog can not view