No products in the cart.
IoT Security - the DVID Challenge - NEW EDITION (W67) - Ethical Hacking Course Online
$299.00 – $365.00
16 items sold
Courses Included
Get the access to all our courses via Subscription
Subscribe
IoT is a growing market and will be the future of our daily lives. Because of its emergence, there is no standard to steward the development process but many protocols and custom solutions to connect hardware to a cloud. Sometimes, a middleware (like smartphone application) could be encountered between hardware and cloud.
COURSE BENEFITS
- What tools will you use?
- What will you get?
- What will you learn?
- What skills will you gain?
- Who is this course for?
- How does it work?
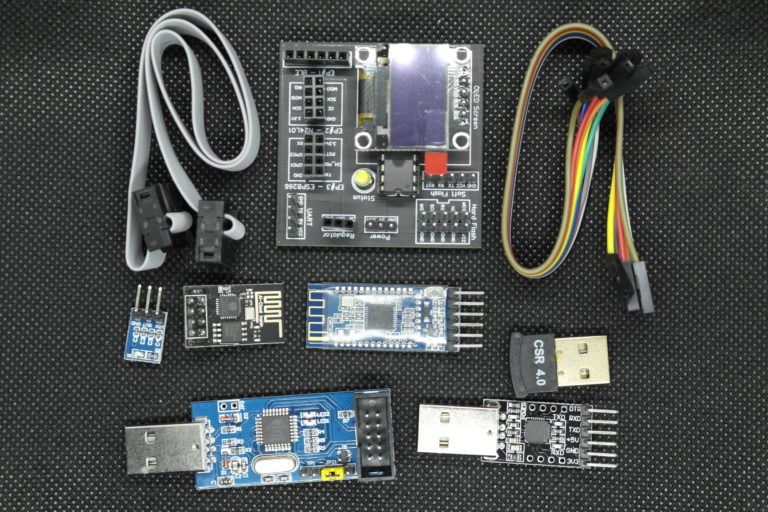
Each attendee will get the Damn Vulnerable IoT Device (DVID) with extension board (Bluetooth), a USBasp to flash the device and USBuart to communicate with the board. For each training, the attendee will flash the device with the corresponding firmware and start to find the solution.
During this course, all materials including slides, transcript and fully detailed step by step correction for training will be provided. For the lab, all runtimes are hosted on attendee’s local machines using docker technology.
This IoT security course will explain IoT concepts, IoT construction and inside security holes. Each attendee will train themself on a dedicated OpenSourced vulnerable board: the DVID project (https://dvid.eu). They will be able to improve their skills to find vulnerabilities and learn how to avoid them during development or starting to hack (with related authorization) real life IoT devices. Because the board is bought by each attendee and still be in the OpenSourced community, attendees could develop other training and get all new published community content for free.
The course is related to the chain of data, not only on the hardware part. IoT is designed to produce data on hardware, control it on middleware (Android/iOS) and present it on the web part (ex.: dashboard). The course includes a Web hacking module to give attendees global knowledge on chain of data security assessment.
After completing the course, each attendee will be able to identify most famous IoT vulnerabilities, like plugging his computer into debug interfaces, analyze outgoing exchange, try to understand protocols used and do some fun tricks with them. They also will be able to write relevant audit reports with vulnerability details and remediation.
From author research, he would like to share his knowledge on IoT Security. This course targets:
- IoT makers in order to help them to develop with security guideline and view impact about security absence
- Security researchers in order to help them to identify the most famous vulnerabilities and be trained with them
- IT Decision maker in order to help him to have appropriate responses when IoT knocks on his IT door
DURATION: 18 hours
CPE POINTS: On completion you get a certificate granting you 18 CPE points.
Course format:
- Self-paced
- Pre-recorded
- Accessible even after you finish the course
- No preset deadlines
- Materials are video, labs, and text
- All videos captioned
IMPORTANT NOTE
To fully participate in this course you need to have the DVID (Damn Vulnerable IoT Device). It is necessary to participate in the class. You can order one pre-made with this course, or manufacture one yourself - see instructions below.
BEFORE YOU START
The board is included in some course purchase options.
All practical works are based on a custom IoT device named DVID (Damn Vulnerable device), designed by the author and published on OpenSource. The main objective is to provide to each interested person a vulnerable board to improve their skill in IoT hacking.
The board core is composed of an Atmega328p SystemOnChip. For each training, a firmware could be flashed on the Atmega328p in order to cover a specific vulnerable environment.
There are also connection ports like UART, Bluetooth and Wifi. In each training, a specific extension board must be plugged in to do the training. Training needs some attack tools like USBasp and USBuart. Many attendees may already have them in person.
In this course, firmware, objectives and solutions are provided free as OpenSource. Moreover, the author will provide a more specific explanation only for this course (step-by-step). The DVID board is shipped from France, only fully assembled and tested. The package contains all tools needed to do all practical works except your favorite pentesting environment (ex.: Kali).
All community content are open source and published on the official Github repository: https://github .com/Vulcainreo/DVID
This board is necessary to participate in the "IoT Security - the DVID Challenge" online course. With some purchase options you'll get a pre-made, ready to go board.
The price includes international shipping, but it does not include any customs fees your country's Customs Office might charge. We are not responsible for getting your package through customs, and if your package is stopped at the border, you will be contacted by the Customs Office to make sure it goes through.
If you have the skills, you can purchase the standalone course (no DVID included), and using the open source schematic and component reference solder everything together. You are responsible for sourcing and financing all components and a naked board. The instructor can provide remote support throughout the process.
Premium subscriber? Order board only >>
Note about shipping
COVID-19: We are shipping normally. Due to restrictions, shipping time might be longer than usual, depending on the origin country. Please exercise all necessary caution when handling packages.
The packages will have tracking enabled, if they are shipped to the following countries: Germany, Saudi Arabia, Australia, Austria, Belgium, Brazil, Canada, South Korea, Croatia, Cyprus, Denmark, Spain, Estonia, United States, Finland, Gibraltar, Great Britain, Hong Kong, Hungary, Ireland, Iceland , Israel, Italy, Japan, Latvia, Lebanon, Lithuania, Luxembourg, Malaysia, Malta, Norway, New Zealand, Netherlands, Poland, Portugal, Russia, Singapore, Slovakia, Slovenia, Serbia, Sweden, Switzerland.
All packages going out to countries outside of this group will have tracking up to the point of arrival in the destination country.
As we have previously experienced issues with customs and delayed/lost packages when shipping to India, we will only be sending boards to India through a premium service (like DHL), which will include extra cost for you to cover.
- Basic knowledge of web and mobile security
- Knowledge of Linux OS
- Basic knowledge of programming - Python
- The DVID (either ordered pre-made here or made on your own; look below for details)
- Mandatory:
- Laptop with at least 50 GB free space
- 8GB minimum RAM (4GB for virtual machine)
- External USB access (min. 2 USB ports)
- Administrative privileges on the system
- Virtualization software
- Optional
- Android phone
- IoT hacking stuff, like logic analyzer, custom IoT devices or probes
The whole course will be organized as follows:
Estimated duration is 18 hours with 7 hours of practical work and 11 hours of lectures. The course will finish with an at home final challenge.
- Module 1: Concepts, protocols and referentials
- Course time: 1 hours
- Practical Work: 1 hour
- Module 2: Hardware and firmware attacks
- Course time: 2 hours
- Practical Work: 3 hours
- Module 3: Middleware
- Course time: 4 hours
- Practical Work: 2 hours
- Module 4: Cloud
- Course time: 2 hours
- Practical Work: 1 hour
- Module 5: Chain of data
- Course time: 3 hours
- Practical Work: 1 hour
- Exam: Escape Game
About the author: Arnaud Courty
 As an IoT expert, my main mission is to evangelize companies to take care about security from the initial design steps. I work on internal and external systems to ensure security analysis and assessment of security maturity of embedded systems upstream their industrialization. Since the beginning of IoT, I have specialized in vulnerability research adapted to embedded systems but also awareness of designers, developers and integrators. I take advantage of security events and working groups to campaign for a less vulnerable IoT world.
As an IoT expert, my main mission is to evangelize companies to take care about security from the initial design steps. I work on internal and external systems to ensure security analysis and assessment of security maturity of embedded systems upstream their industrialization. Since the beginning of IoT, I have specialized in vulnerability research adapted to embedded systems but also awareness of designers, developers and integrators. I take advantage of security events and working groups to campaign for a less vulnerable IoT world.
Course Syllabus
Module 1: Concepts, protocols and referentials
This module will cover concepts and basic knowledge about IoT. After presentation of well-known IoT protocols, the course will explore IoT architecture, related referentials IoT security and get your foot in the door with discovering the Practical Work board (DVID board).
- Communication protocols
- UART
- JTAG
- SPI
- I2C
- CanBUS
- Zigbee
- Generalities
- Security VS safety
- Security objectives and definition
- Embedded system life cycle
- Architecture
- Hardware level
- Software level
- Communication level
- Security level
- Focus on SecBus architecture
- References:
- OWASP
- GSMA
- ETSI
- Other initiatives
- Discovering an IoT object (TP board)
- Discovering methodology
- Hardware identification and information gathering
- Making a reverse engineering schema
- Attack vectors
- Discover the practical work board DVID: Attendees will discover the practical work platform, discovering the DVID board, trying to interact with it and send first bytes of data.
Module 2: Hardware and firmware attacks
This module will cover hardware and firmware attacks. After discovering all available attacks, the course will explore and train vulnerabilities on the DVID board.
- Definition (Embedded system, RTOS, firmware, kernel space or bootloader) • File systems
- Analysis
- Firmware extraction
- Firmware analysis (binwalk/FMK)
- Static analysis
- Firmware attacks
- Hardware attacks introduction
- Basic and PCB building
- Recon
- Analysis (Static, Dynamic)
- Hardware attacks
- Side channel attacks - Timing attacks
- Memory spying attacks
- On bus attacks
- Fault injections
- Hardware reverse engineering
- Counter measures
- Pentesting
- Methodology
- Top 10 OWASP on IoT Security
- Remediation and best practices
- Find the datasheet: Attendees should explore public information in order to set up a working connection to the DVID board and get the flag.
- Analyze the firmware: Attendees will explore firmware analysis to retrieve the root password.
- Hardcoded password: Attendees should retrieve the confidential message by extracting and analyzing firmware.
- Default password: Attendees should build a bruteforce attack to retrieve the right password.
- EEPROM: Attendees should explore EEPROMstructure to solve the challenge.
Module 3: Middleware interactions
This module will cover middleware interactions from hardware to cloud. After discovering a well known protocol, the course will explore and train about IoT usage and available attacks.
- MQTT
- Presentation
- Playing with the protocol
- Attacks
- Presentation
- Bluetooth Low Energy
- Bluetooth history/evolution
- Advertising Concept
- Characteristics & services Concept
- Playing with the protocol
- Communication pairing/encryption
- ibeacons
- CoAP
- Protocol Presentation
- Models
- Message
- Playing with the protocol
- Android
- Architecture application and system
- Application components
- Security
- Pentesting methodology
- Pentesting
- Methodology
- TOP 10 OWASP Mobile device
- Remediation and best practices
- MQTT - Meetings: Attendees will explore MQTT by getting sensitive information about secret meetings.
- MQTT - Open the door: Attendees will explore MQTT by interacting with a remote door locker.
- MQTT - RCE: Attendee will find vulnerabilities to take over the MQTT broker.
- BLE - Advertising: Attendee will explore advertising on BLE to get sensitive information.
- BLE - Characteristics: Attendee will explore BLE characteristics to read data to the remote device.
- BLE - Characteristics 2: Attendee will explore BLE characteristics to write data to the remote device.
Module 4: Cloud interaction
This module will cover cloud interaction from a device or device through a middleware. After discovering well known vulnerabilities, the course will explore and train about IoT specific vulnerabilities.
- Cloud architecture
- Characteristics and model
- Architecture example
- Threat identification
- Vulnerabilities identification
- Injection
- SQL code injection
- NoSQL code injection
- Weakness in authentication and session management
- Session cookies
- Captcha
- Session management
- Cross Site Scripting
- Weakness in access control
- Weakness in configuration
- Sensitive information exposure
- Directory listing
- Direct file access
- Filename prediction
- Weak protection against attacks
- Absence of cryptography
- Absence of brute force protection
- Cross-Site Request Forgery (CSRF)
- Public vulnerabilities (lack patch management)
- Denial of service
- Insecure cache management
- Injection
- Rest API Analysis
- Definition (API, WSDL, Soap and REST)
- JWT token
- Pentesting
- Concept presentation
- Pentesting Web methodology
- Information gathering
- Infrastructure analysis
- Application analysis
- Pentesting API methodology
- Finding endpoints
- Finding documentation
- Common vulnerabilities
- JWT focus
- Security best practices
- Web application
- API application
- CSRF attack: Attendee should analyze the application to find the CSRF vulnerability.
- SQL injection attack: Attendee should analyze the application to get the admin hashed password by exploiting a SQL injection vulnerability.
- Cookie stealing: Attendee should analyze the application to find a possibility to extract the user’s cookie to the attacker's server in order to impersonate the user session.
- API - Business workflow: Attendee should understand internal API workflow to find vulnerabilities in suspicious malicious behavior.
Module 5: Chain of data
This module will cover a chain of data. The course will explore the whole process of data from device production to cloud consumption. In this module, you will be more comfortable about sensibility of data and how to protect it with correct infrastructure.
- Cloud provider
- AWS IoT Platform
- Microsoft Azure IoT Hub
- IBM Watson IoT Cloud Platform
- Google IoT Cloud Platform
- Real life architecture
- Availability oriented implementation
- Confidentiality oriented implementation
- Integrity oriented implementation
- Traceability oriented implementation
- Pentesting
- Methodology
- Real life example
- AWS Cloud ready device: Attendee should explore the security of device built AWS IoT cloud ready
- Very secret wallet: Attendee should explore the security of a “very secret wallet” to find a way to get private data of the owner.
Exam: Let’s assess the security of an IoT device
- In this exam, attendees will be in front of an IoT device. This device is a temperature sensor, located in datacenter racks. This sensor communicates temperature value to an Android appliance over Bluetooth. This appliance is located outside the datacenter door and communicates temperature values to the cloud server over MQTT protocol.
- All learnt skills about hardware analysis, middleware reverse or cloud exploration are needed to analyze the security of this IoT device.
- In order to pass the exam, all flags need to be found. However, attendees who would like to write a relevant report will be thanked for their work and will receive a special access to the full version of this EscapeGame.
QUESTIONS?
If you have any questions, please contact our eLearning Manager at [email protected].
FAQ
ABOUT THE DVID:
The DVID (Damn Vulnerable IoT Device) is an intentionally vulnerable IoT device to help you learn about IoT security.
Yes. Without it you won’t be able to do any practical work throughout the course, a big part of the content will refer directly to it as well.
You can order a premade device with us, or you can make one yourself (buy all components and solder them together). For all instructions see the course description.
The DVID is manufactured by the instructor of the course, Arnaud Courty.
Yes. All boards are thoroughly tested before shipping, as well as all components and attack tools provided with the device.
No, we don’t offer part-only packages for retail customers. It is possible for group orders - see “Special orders” section.
SHIPPING:
Shipping will be done worldwide, but tracking will be available only for specific countries.
The packages will have tracking enabled, if they are shipped to the following countries: Germany, Saudi Arabia, Australia, Austria, Belgium, Brazil, Canada, South Korea, Croatia, Cyprus, Denmark, Spain, Estonia, United States, Finland, Gibraltar, Great Britain, Hong Kong, Hungary, Ireland, Iceland , Israel, Italy, Japan, Latvia, Lebanon, Lithuania, Luxembourg, Malaysia, Malta, Norway, New Zealand, Netherlands, Poland, Portugal, Russia, Singapore, Slovakia, Slovenia, Serbia, Sweden, Switzerland.
All packages going out to countries outside of this group will have tracking up to the point of arrival in the destination country.
We have previously experienced issues with customs and delayed/lost packages when shipping to India. For this reason, if you want to order the board, we will only be sending it through a premium service (like DHL), which will include extra cost for you to cover.
We will be contacting you by email with further instructions.
Since the boards are manufactured just for this course, we will contact you with specific details after you order. You will be notified when the shipment is made.
Please document the package and contact our e-Learning manager at [email protected]@hakin9.org
Please document the board and contact our e-Learning manager at [email protected]@hakin9.org
If you received a notice from us confirming that we’ve sent the package and the shipment does not arrive after a reasonable amount of time, please contact our e-Learning Manager at h9.courses@hakin9.org
I AM A HAKIN9 PREMIUM SUBSCRIBER / IT PACK PREMIUM SUBSCRIBER / LIFETIME SUBSCRIBER
Yes, the course is included in your subscription, but the board is not. Don’t worry, we have a special product made just for you, where you can purchase the pre-made board independently from the course: https://hakin9.org/product/board-only-dvid-challenge-w46/ You can also manufacture the board yourself, if you’re feeling up to it - see instructions in the course description.
No. The BOARD ONLY product includes only the pre-made board and course access is not included. You have course access through your premium subscription.
No, you should either purchase a seat on the course, or renew your subscription.
Yes, you will be able to view the training materials and see the assignments. However, you won’t be able to perform any practical exercises from the course, unless you make the board yourself (instructions provided in the course description).
SPECIAL ORDERS
My University would be interested in enrolling our students in this course. Are there any discounts?
Educational institutions receive a discount for course enrollment. The price of the DVIDs (if you choose to order them as well) will not be discounted. Please contact our Product Manager Marta Sienicka at [email protected] for further details.
You can make a bulk order, but the price will not be discounted - the price of the DVID as offered on the website includes bare manufacturing and shipping costs. Please contact our Product Manager Marta Sienicka at [email protected] for further details.
Yes, provided you meet certain criteria in regards to the amount of the packages you want. Please contact our Product Manager Marta Sienicka at [email protected] for further details.
Companies receive a discount for group course enrollment only. The price of the DVID (if you choose to order it as well) will not be discounted. Please contact our Product Manager Marta Sienicka at [email protected] for further details.
You can make a bulk order, but the price will not be discounted - the price of the DVID as offered on the website includes bare manufacturing and shipping costs. Please contact our Product Manager Marta Sienicka at [email protected] for further details.
Yes, provided you meet certain criteria in regards to the amount of complete packages you want. Please contact our Product Manager Marta Sienicka at [email protected] for further details.
RETURNS & REFUNDS
Please document the package and contact our e-Learning manager at h9.courses@hakin9.org. We offer replacements if you meet the criteria for one.
Please document the board and contact our e-Learning manager at h9.courses@hakin9.org. We offer replacements if you meet the criteria for one.
You can only return undamaged boards within 14 days of receiving them. You have to inform us of your intent to return within that time frame, by email at h9.courses@haking.org. You are responsible for the return shipment and its cost. It should be made to a return address we provide. You must provide us with proof of shipment within 7 days of informing us of intent to return. After we receive your return package, the board will be evaluated for damage, and if everything checks out, we’ll reverse your payment.
Yes. You can only return undamaged boards within 14 days of receiving them. You have to inform us of your intent to return within that time frame, by email at [email protected]. You are responsible for the return shipment and its cost. It should be made to a return address we provide. After we receive your return package, the board will be evaluated for damage, and if everything checks out, we’ll reverse your payment.
Yes, if you meet the criteria. For our return policy for online courses, please refer to our Terms of Service.
Yes, if you meet the criteria. For our return policy for online courses, please refer to our Terms of Service.
Only logged in customers who have purchased this product may leave a review.





Reviews
There are no reviews yet.