No products in the cart.
The Tor project allows users to surf the Internet, chat, and send instant messages anonymously through its own mechanism. It is used by a wide variety of people, companies and organizations, both for lawful activities and for other illicit purposes. Tor has been largely used by intelligence agencies, hacking groups, criminal activities and even ordinary users who care about their privacy in the digital world.
Nipe is an engine, developed in Perl, that aims on making the Tor network your default network gateway. Nipe can route the traffic from your machine to the Internet through Tor network, so you can surf the Internet having a more formidable stance on privacy and anonymity in cyberspace.
Currently, only IPv4 is supported by Nipe, but we are working on a solution that adds IPv6 support. Also, only traffic other than DNS requests destined for local and/or loopback addresses is not trafficked through Tor. All non-local UDP/ICMP traffic is also blocked by the Tor project.
More: https://github.com/htrgouvea/nipe
Download and install
# Download
$ git clone https://github.com/htrgouvea/nipe && cd nipe
# Install libs and dependencies
$ sudo cpan install Try::Tiny Config::Simple JSON
# Nipe must be run as root
$ perl nipe.pl install
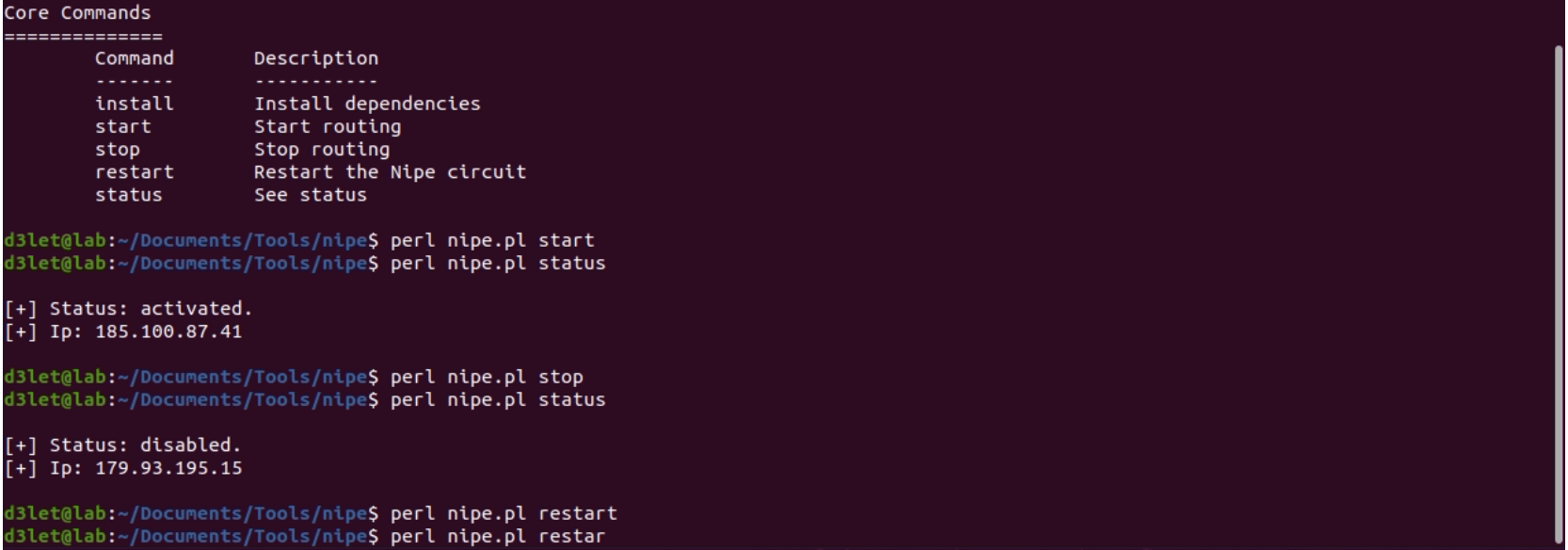
Commands:
COMMAND FUNCTION
install Install dependencies
start Start routing
stop Stop routing
restart Restart the Nipe circuit
status See status
Examples:
perl nipe.pl install
perl nipe.pl start
perl nipe.pl stop
perl nipe.pl restart
perl nipe.pl status
Demo
Contribution
-
Your contributions and suggestions are heartily ♥ welcome. See here the contribution guidelines. Please, report bugs via issues page and for security issues, see here the security policy. (✿ ◕‿◕) This project follows the best practices defined by this style guide.
-
If you are interested in providing financial support to this project, please visit: heitorgouvea.me/donate

A very big thanks to kelvinethicalhacker at gmail com for the great the work you done for me, i got the email address on the net web when i needed to hack my husband cell phone he helped me within few hours with whatsApp hacking and GPS location tracking direct from my person phone i know how my husband walks, thanks for the helped you do for me for every grateful for your helped, you can contact him through gmail via kelvinethicalhacker at gmail.com or Telegram, calls, text, number +1(341)465-4599, if you are in needed of hacking services, contact him..
A great hacker is really worthy of good recommendation , Henry
really help to get all the evidence i needed against my husband and
and i was able to confront him with this details from this great hacker
to get an amazing service done with the help ,he is good with what he does and the charges are affordable, I think all I owe him is publicity for a great work done via, Henryclarkethicalhacker at gmail com, and you can text, call him on whatsapp him on +12014305865, or +17736092741,