No products in the cart.
Dear Readers,
We prepared for you new issue "Investigating Security implications of data hiding techniques under Windows OS"
Author: Nihad Hassan
"Investigating Security implications of data hiding techniques under Windows OS"
What you will learn:
Using a variety of techniques to hide data under Windows Operating System
Using these techniques to exploit Windows systems
Understanding Alternative Data Stream files concept and its security implications
What you should know:
Understanding of Windows OS working and main functions.
Basic Knowledge of MS DOS commands.
The art of data hiding is concerned about putting data where it is not supposed to exists, current operating systems and file structures give us vast possibilities to conceal our data and making it harder to detect, a person with a malicious intent can also use these techniques to bring damage to our system. The internet is full of articles that talk about this subject, however few of them discuss data hiding under Windows OS in a more simple language as we try to achieve in this article.
Data hiding could be done using variety of methods and techniques, I will begin my discussion in describing simple but yet efficient methods to hide data within files and system structure. The methods Iam going to explain in this article are as follow:
A. First: Simple Methods
1. RTF documents,
2. Renamed files,
3. Hiding data in Registry,
4. Hiding in Microsoft Office documents.
B. Second: Advanced Methods
5. Alternative Data Streams,
6. Stealth Alternative Data Streams,
7. Shadowing.
1-RTF documents [1]:
Rich Text Format (RTF) files is a property file documents developed by Microsoft , it could be opened and edited using both WordPad and MS Word program (all versions), there are many versions of RTF specifications and it is continually developed with each release of Microsoft office suite.
RTF use a similar markup language to HTML, this leaves a room for hiding data inside some of its tags, it is seldom for a user to check the raw data of RTF file and this makes it very suitable for hiding data with limited possibility of being discovered.
To view the raw source data of RTF file, we can open it using Windows notepad, we notice that RTF file begins with {rtf1 and end with } . All data exists after the closing bracket is ignored and not displayed when viewing RTF files using Word or WordPad. RTF also ignore any text located between { and } inside the document body, which make this location also suitable for hiding data inside it.
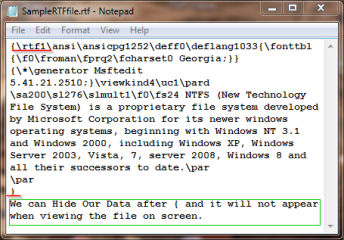
Figure 1: Hiding data inside RTF file raw data source
2-Renamed Files [2]:
We can change file extension and store it inside c:WindowsSystem32 directory, for example, if we want to hide a word file called invoice.doc , we can change its name to MSDOS386.dll , System32 directory is full of DLL files and Windows by default change the ICON and default associated program used to open the file according to its new extension, thus making it nearly impossible for casual user to discover the trick.
The only possible way to recognize renamed files is to check file signature, under Windows OS each file extension has a unique signature usually stored in the first 20 bytes of the file, we can check the original file signature of any file through opening it using notepad. For example EXE, DLL, SYS extensions have the signature (MZ) , RTF documents ({rtf1) , word files 2007 (PK••••••) and Word 2010 built with open XML format (PK••).
3-Hiding Data in Registry [3]:
We can hide data of different format within Windows registry (strings, binary data), some registry entries are already available for storing hidden data , the best known location is HKEY_LOCAL_MACHINESystemCurrentControlSetControlTimeZoneInformation , this key records the difference between PC local time and UTC time zone in addition to other functions. This key contains two entries that could hold both string and binary data and could be left empty as they are not used by Windows. These entries are StandardName and DaylightName.
We can also create a new key under TimeZoneInformation key and create different values inside it to hide our data (of course we should use misleading names for our values to make discovering our hidden keys more difficult).
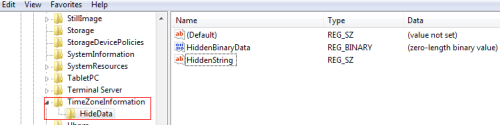
Figure 2: Adding new key under TimeZoneInformation key to hide different data formats
4-Hiding Data in Microsoft Office Documents:
We can hide data in MS Office Word document using a variety of ways:
using extra small font size,
using white color (over white background),
using hidden font property (Highlight text >> Font >> Hidden),
meta Data (insert data in file properties – author name, comments ...etc.),
OLE Structured Storage (merging two office documents in one stream),
hiding inside document structure (only supported on MS office 2007 and above).
We will discuss the last two methods in some detail.
OLE Structured Storage [4]:
According to Wikipedia OLE Structured Storage is:
“COM Structured Storage (variously also known as COM structured storage or OLE structured storage) is a technology developed by Microsoft as part of its Windows operating system for storing hierarchical data within a single file. Structured storage is widely used in Microsoft Office applications”. Using this technology we can hide one word document inside an excel document or vice versa , we can perform this using a free tool called merge stream from this website https://www.ntkernel.com and it support the following Windows OS: 9x, ME, NT 4.0, 2000, XP.
Install the tool, select two files, one MS Word and another MS Excel and finally click the “Merge” Button as follow
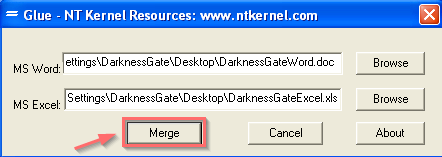
Figure 3: Merging two different office documents using merge stream tool
After clicking the “Merge” button, if everything is OK the following success message will appears:
Now both documents will be merged into a single file. In order to open the excel file we need to rename the extension of the word file to .xls because the excel file is now hidden inside the word document, we can reverse the case if we want either. Please note this technique is only supported on MS office suit version 2003 and below, newer versions of MS Office files are not supported because it is not a binary file.
Hiding inside document structure [5]:
Newer office suite (2007 – 2010 - 2013) are built using the open XML file format, this format consists of a zip file that contains many XML and binary files and has the DOCX extension, if we unzip this file we can have a folder named with the same file name and contains three folders and one XML file in the main directory named [Content_Types].xml.
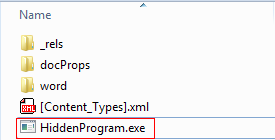
Figure 4: Content of Word document (2007 and later version) after unzipping it
Open [Content_Types].xml and add this line to the end of the file before the tag:
Where HiddenProgram.exe is the name of the program or file that we want to hide inside the Word file (it could be any file type), now we need to put our hidden program in the main directory (as we did in figure 4) and Zip the folder again and rename its extension to DOCX, this method encapsulate our Word document with another file/program hidden inside it.
5-Data hiding using alternative data stream:
Before we begin our discussion on data hiding using alternative data stream files, we need first to briefly describe the file system structure that supports this feature which is the NTFS file system.
What is NTFS File System?
NTFS (New Technology File System) is a proprietary file system developed by Microsoft Corporation for its newer Windows operating systems, beginning with Windows NT 3.1 and Windows 2000, including Windows XP, Windows Server 2003, Vista, 7, server 2008, Windows 8 and all their successors to date.
NTFS supersedes the FAT file system as the preferred file system for Microsoft’s Windows operating systems. NTFS has several improvements over FAT and HPFS (High Performance File System), such as improved support for metadata, compression and auditing, and the use of advanced data structures to improve performance, reliability, NTFS supports large volumes and powerful storage solution such as RAID, plus additional extensions, such as security access control lists (ACL) and file system journaling. NTFS has the capability to encrypt or decrypt data, files, or folders; it uses a 16-bit Unicode character system set to name files and folders allowing users from all over the world to use their native language to name files & folders. The main purpose from creating this new file system was maintaining the compatibility with Macintosh Hierarchical File System (HFS) and to store additional data about each file called the metadata and this what we are going to use to hide our data.[6][7]
Note: during this article I use the shortcut ADS instead of Alternate Data Streams.
What is an alternate data stream (ADS)?
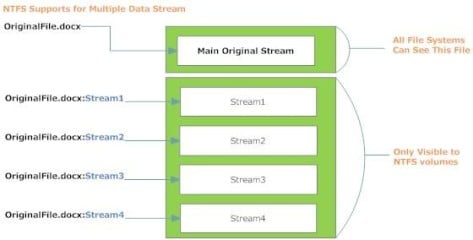
In NTFS, a file consists of different data stream, one stream is the primary unnamed stream which contains the visible data that we expect to see in a file after opening it, this stream is usually called the default stream and it is referenced when no stream name component is specified as a part of the pathname. The second stream is the alternative data streams; a file can have more than one ADS stream (Microsoft does not supply the number of allowed ADS files per a single file but a test conducted by Jason Fossen suggests that the maximum is 4106 regardless of the size of the ADSs themselves[8]), for example: one stream can hold file security information such as access permission , another stream can hold other meta data about the file, for example: Word file can have a number of properties like: author , number of words , number of pages , date created and so on. These alternative data streams could be accessed by referring to their names, all these streams are linked to the main default stream of one file (normal visible file).
ADS files has the ability to be appended to existing files without affecting their size or functionality, ADS files also are not visible to windows explorer or to (DIR) command (unless we use the /R switch).If we append a malicious software (virus or Trojan) as an ADS file, it could be executed by using the (start) command (only windows XP supports executing ADS binary files through this command , newer Windows OS require another command to handle this issue as we will see later on), once executed by the user ,it can install the malicious software on its PC with silent installation , no process will appear in the process list of the Windows task manager as the program which is used to open the original file (default stream) will appear in the process list but not the malicious program, beside we can attach the malicious program to a legitimate process and executing it making it more difficult to detect.
As we note from figure 5, we have 4 ADS files for a single file, any of the streams (from Stream1 to Stream4) can hold malicious software (Trojan, rootkit, virus) appended to the default main stream (visible file OriginalFile.docx) without affecting its size or function.
How we can use ADSs to hide files?
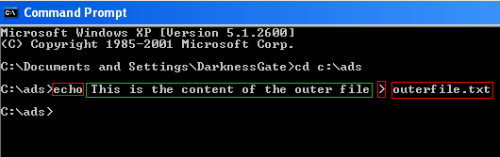
To show how we can use ADS to hide files, I will make an example. Create a new folder under the C: drive and call it (ads), open command prompt and change your working directory to (C:ads) folder. Create a text file called (outerfile.txt) using DOS as follow
I marked the content of the file with green, the(echo) and (>)command tell DOS to create a file with the specified contents and output the result to the file named (outerfile.txt) , this file will be outputted on (C:ads) as it is the current working directory as appeared in DOS window.
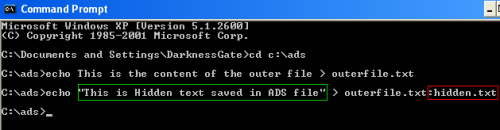
Figure 7: Creating hidden ADS file and appending it to outerfile.txt
Now I want to create the hidden ADS file, I use the same commands to create another text file, the colon is the syntax used to create an ADS file. Use the (dir) command to check all the files existed inside the (ads) folder as follow:
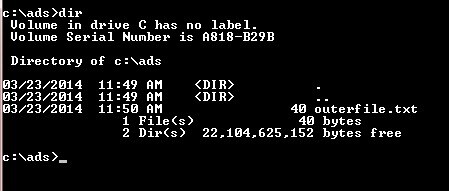
Figure 8: listing c:ads directory files
We have only one file called (outerfile.txt), while the other file (ADS file) is hidden.
The file hidden in the ADS cannot be seen using (dir) or Windows Explorer, but Notepad can open it and display the contents of the file.
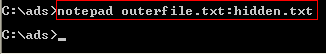
Figure 9: Opening hidden ADS file
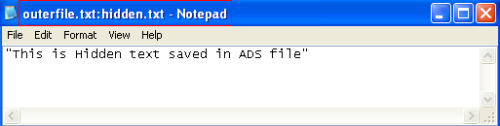
Figure 10: hidden.txt opened using notepad from command line
In the same way we can copy one file to become hidden inside another file using ADS as follow:
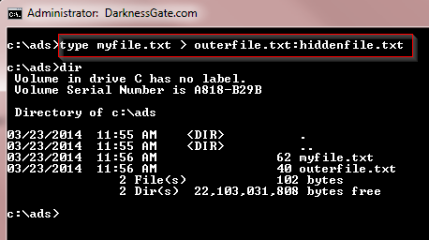
Figure 11: hiding a file within another file using ADS technique
(Type) command is used to copy the (myfile.txt) content to be included in the alternative stream of (outerfile.txt) under the name (hiddenfile.txt).
You can make a ADSs in not only files, but also directories, here is an example:
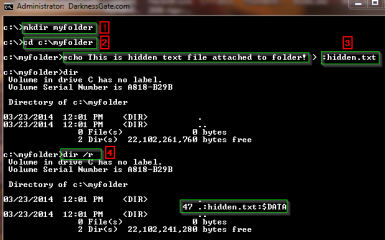
Figure 12: Hiding data in a directory using ADS
First line I created a directory on the C: called (myfolder),Second line I changed my working directory to C:myfolder , third line I created a hidden text file (hidden.txt) using the colon: and hide it inside the (myfolder) folder as a file stream which is my working directory. Using the DIR command alone does not show the hidden stream associated with current directory, we should use the /R switch to make it visible.
We can open this hidden file using notepad as we did previously
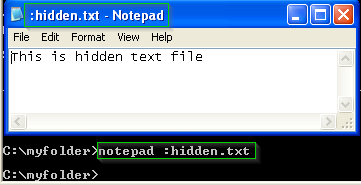
Figure 13: Open hidden ADS file attached to a folder
Hiding Executable in ADS files:
The most interesting feature about NTFS file system and its associated ADS files is the ability to hide executable (binary files) inside the stream, Windows XP supports running executable within ads stream files directly using the (start) command, however beginning from Windows vista, Microsoft has removed this ability for security purposes, however we are still able to hide our binary file and executing it through using symbolic link or WMIC command prompt in newer Windows OS.
The (start) command works on Windows XP only when used to lunch binary files in hidden ADS, it is not supported by Vista, 7 and later versions, however we can still execute binary files stored inside ADSs stream through using symbolic links or WMIC command, the following lines describes these methods under Newer Windows OS (Vista , 7 , 8).
Let’s examine a scenario where an attacker successfully compromise a remote system or simply gain physical access to the victim PC, the attacker wants to run a password cracking tool in stealth mode without leaving any traces, the password cracking tool should be hidden in ADS file and executed from a USB drive formatted as NTFS, a list of saved passwords should be stored as a text file hidden inside an ADS file.
Nirsoft https://www.nirsoft.net develops many windows portable applications specialized in password recovery, one of these tools called MessnPass and it is specialized in recovering passwords of all famous instant messenger applications, we will use this tool in our example under Windows 7
First we hide mspass.exe into an ADS hidden stream of outerfile.txt file under the name password.exe , next step we create a symbolic link (run.exe) , as we are not able to execute binary files inside the hidden stream using the (start) command under windows 7 , but we still able to execute the symbolic link (run.exe) , the mspass.exe tool has a specific switch to store its output into a text file (/stext) , we use this switch to store all recovered passwords into a text file ([email protected]) and hide this file directly inside another one (garden.doc).
Important notes about using ADS in hiding files:
If we delete the main file (primary stream) , the associated ADSs files will be deleted either,
We cannot set permission or any additional attributes to the ADS file, because ADS relies on the attributes associated with the primary stream file,
Any new permission or attributes (like the hidden attrib) to the main file (primary stream) will also affect the ADS associated files,
ADS files can only be created on system with NTFS file formatting, FAT file system and other types of file systems are not supported,
The primary stream could be any type of files like PDF, folders, MS office files, videos, images, executable etc…,
Most antivirus software do not scan Windows Alternate Data Streams for virus, and other malicious code by default, if you suspect a file is containing a malicious code in its ADS file make sure to use “Method one” described below in the “How to delete ADS files”, the first method is the best secure one as some ADS files could be hidden from the detection tools either,
Windows does not provide any built in utilities to detect the existence of ADS files,
we can attach more than one hidden ADSs file into one primary stream (We can have 4106 ADS files according to Jason Fossen study[8]).
How to delete ADS files:
In case we want to delete the ADS file and we still want to keep the main stream file we can do the following:
Mehtod1:
Copy the main stream file to another disk which has FAT formatting, if the file is not too big we can move it to a flash memory with FAT file system and then moving it again to the NTFS partition, in this case the hidden ADS stream is deleted because it will not move to the FAT partition.
A warning message appears when trying to copy a primary file stream associated with ADS file into FAT partition
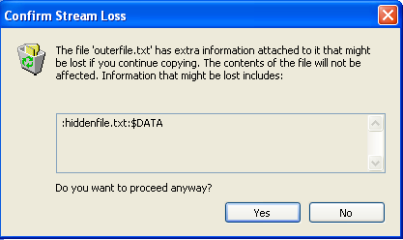
Figure 14: Warning message after moving a file with ADS stream to a partition with FAT formatting
This is the best method as it can delete all ADS files even thought it was from the stealth type (as we will see in next section on stealth ADS files).
Mehtod2:
The second method to delete the ADS file while preserving the primary stream is through copying the main file into a temporary file and then deleting the original file and renaming the temporary file again to its original file name.
Detecting ADSs file stream:
Windows operating system does not provide any utility to detect ADSs files on NTFS disks; fortunately we have many free tools for doing this job
LADS
This program lists all ADS files of a NTFS directory; it works from command prompt as follow:
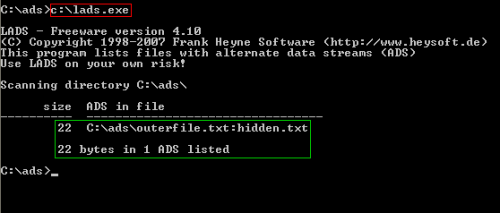
Figure 15: Using Lads.exe tool to check hidden ADS files
Lads program is located at C: drive, we navigate to the folder where we want to check the ADSs file stream and executes the lads.exe tool , the above results appears.
Streams.exe from SysInternals:
We can execute this tool from the command line as follow to detect hidden ADSs streams in files in specific folder/drive
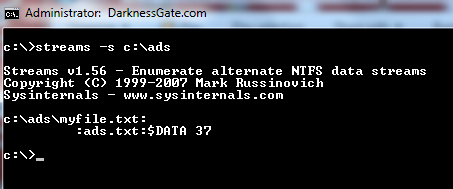
Figure 16: Using streams.exe from system internals to detect ADS files
In Figure 23 Iam checking (C:ads) for hidden ads streams.
6-Stealth Alternative Data Stream:
Microsoft select a set of reserved names to be used for its connected hardware devices Output operations (like printer use LTP) or to enables software components to communicate (use COM), these names are CON, PRN, AUX, NUL, COM1, COM2, COM3, COM4, COM5, COM6, COM7, COM8, COM9, LPT1, LPT2, LPT3, LPT4, LPT5, LPT6, LPT7, LPT8, and LPT9[10]. We can make more stealth ADS files which is not detectable by tools like lns.exe (https://ntsecurity.nu/toolbox/lns), Streams.exe (www.sysinternals.com/utilities/streams.html) ,Ad spy (https://www.bleepingcomputer.com/download/ads-spy/ ) , sFind (https://www.mcafee.com/us/downloads/free-tools/forensic-toolkit.aspx), or regular DOS commands (DIR and DIR /r) through naming our ADS file with one of these reserved names. After testing all known ADS detection tools, only Lads.exe was able to detect ADS stealth stream files.
Figure 17: Error messages after attempting to name file or folder with reserved Windows names
As we note from Figure 24, attempting to create a file or directory with any of the reserved names mentioned before generate an error.
Before saving any file or directory to the file system under Windows , the OS performs a check on the validity of the name using NT-style name rules , these rules check for name , path length (255 characters maximum) in addition to the existing of periods inside the path name. In order to override this naming rules limitation we use the prefix (\?) , for file I/O, putting the (\?) prefix to a path string tells the Windows APIs to disable all string parsing and to send the string that follows it straight to the file system[10]
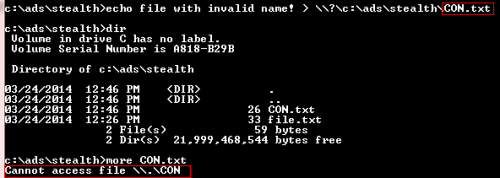
Figure 18: Creating a file with reserved Windows name
We create a file with reserved Windows name called CON.txt, but when trying to open it I get a message (Cannot access the file) , to read this file we need to use the prefix (\?) again
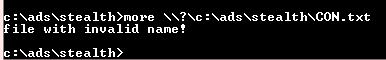
Figure 19: Reading a file with reserved Windows name
Now we combine both methods, creating a file with reserved Windows device name and appending an ADS file stream to it, this create what is called “Stealth Alternative Data Stream” , this approach allow users to create completely hidden ADS files which are not easily detected , most ADS detection tools , DOS commands (DIR and DIR /r) are not able to uncover the hidden streams within these files, some anti-virus software do not scan stealth ADS, we can also hide malicious software , malware inside the hidden file as we did in previous section and use the same techniques described previously to lunch executable hidden inside ADS files , here is a quick example of hiding a Windows calculator inside a Stealth hidden ADS and lunching it later using the WMIC command.
7-Volume Shadow Copy Data Hiding [14]:
Volume shadow copy (VSS) is a service available in both Windows 7 and Vista OS, it coordinates the actions that are required to create a consistent snapshot copy of the data to be backed up in a specific volume in a specific point-in-time over regular intervals. We can access this feature through the system restore functionality , which enable us to restore our system files to a previous stable state in case of sudden system failure (for example: failed software installation OR wrong uninstallation of some programs , wrong system registry modifications). Shadow copy technology works only on Volumes formatted with NTFS, and the shadow copies created could be stored on local or external networks as needed [11][12].
The snapshots created by VSS (restore points) are taken at specific time intervals, usually after installing/uninstalling new software or performing a system update, it is difficult to predict the other cases when the VSS create a snapshot, however there are some conditions for this to happen as the system should be idle for at least 10 minutes , and it should be running on AC power (if it is portable) , if the two conditions happened together we can expect to have a system restore point every two days under Windows Vista and between 7 to 8 days under Windows 7. Of course you can still create system restore points manually if you would so [13].
It is important to note that shadow copy is not an image of the entire drive, VSS operates on the block level (below file system level), VSS is tracking any changes made to all blocks on the volume, when a specific block has data written to it,VSS makes a snapshot and store it in a hidden volume (these snapshot is read only). If a specific block hasn’t changed since the last snapshot, it will not include in the current snapshot (restore point). VSS is incremental (like the incremental backup concept of databases), it will only store the modifications that happen to one file since the last snapshot.
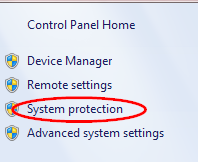
To configure VSS service under Windows 7 we can access it from System >> Properties >> System Protection
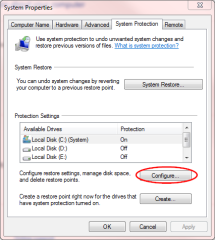
Figure 20: Configuring restore points under Windows 7
Through the “Configure” button we can choose to activate Volume shadow service, manage allocated space and restore points for each listed volume.
This introduction is necessary to understand how VSS works, now we can explore the VSS snapshots potential in hiding data or other malicious software.
We can administer VSS thorough using the VSSadmin utility that comes with both Vista and Win 7 OS, lunch a DOS command and type (VSSadmin) to view command switches, type (VSSadmin list volumes) to list all available NTFS volumes on your system eligible for shadow copies.
The command (VSSadmin list shadowstorage) enable us to see the shadows and disk usage of our system's volumes, in my case I have only the c: volume with has VSS enabled.
In summary, we found that we can hide data inside system restore points, if these data is executable application we can run it using the WMIC command without creating any symbolic links , most anti-virus software do not scan volume shadow copies for malware and other security threats , it is important to remember that volume shadow copies are limited in space and time , if you store large files inside it , system needs to delete the old restore points to give room for newly created one , however , if your files was small and you are a regular PC user , a restore point may last for at least 5 months under Windows 7 and this is more than enough for a hacker to perform evil actions against your PC.
Conclusion:
It is crucial to understand how data could be hidden inside file system structure, this knowledge will allow us to understand the potential risks and how hackers could use such techniques to hide malicious files and exploit our system.
This article discussed various methods of hiding data using Windows OS, the methods discussed were presented using simple illustration to make it easy to understand by casual user, however, we did not cover the whole spectrum of this advanced subject (we need a book for this!), there still many more techniques could be used for hiding data such as:
1. File Slack (both RAM and disk slack),
2. Volume Slack (space between partitions),
3. Partition slack , where leftover sectors remain in stored blocks of data,
4. Marking drive blocks as bad sector and using it for data hiding,
5. Host protected area and vendor specific drive space,
6. Master boot record (MBR),
7. Boot sectors in non-bootable partitions,
8. Setting file or folder attributes as hidden (attrib +s +h),
9. Using Steganography,
10. Hiding data within HTML files,
11. Encrypting files,
12. Hiding in compressed files.
New methods of data hiding will continue to evolve as technology advance, this require us to continue developing our skills to stay current with the latest threats.
Full version in Hakin9 soon!
References:
[1]Wikipedia website , Rich text format files. Available at:
https://en.wikipedia.org/wiki/Rich_Text_Format [Accessed 2014/03/22].
[2]File Signature Database .Available at: https://www.filesignatures.net/ [Accessed 2014/03/22].
[3]Harlan Carvey (2004). Windows Forensics and Incident Recovery. Chapter 3. Addison-Wesley Professional.
[4]Wikipedia website , COM Structured Storage. Available at: https://en.wikipedia.org/wiki/COM_Structured_Storage [Accessed 2014/03/25].
[5]Telos website , Hiding data in documents. Available at: https://multimedia.telos.com/blog/hiding-data-in-documents-the-insider-threat-revisited [Accessed 2014/03/18].
[6]Microsoft TechNet , How NTFS works. Available at: https://technet.microsoft.com/en-us/library/cc781134%28v=ws.10%29.aspx [Accessed 2014/03/18].
[7]Wikipedia website .NTFS files system. Available at: https://en.wikipedia.org/wiki/NTFS [Accessed 2014/03/18].
[8]Data Hiding Tactics for Windows and Unix File Systems .Available at: https://www.berghel.net/publications/data_hiding/data_hiding.php [Accessed 2014/03/19].
[9]Figure 5: adopted from Microsoft TechNet website . Available at: https://technet.microsoft.com/en-us/library/cc781134%28v=ws.10%29.aspx [Accessed 2014/03/18].
[10]MSDN website . Naming Files, Paths, and Namespaces. Available at: https://msdn.microsoft.com/en-us/library/aa365247%28VS.85%29.aspx [Accessed 2014/03/25].
[11]Wikipedia website . Shadow Copy. Available at: https://en.wikipedia.org/wiki/Shadow_Copy [Accessed 2014/03/26].
[12]Microsoft TechNet . Volume Shadow Copy Service. Available at: https://technet.microsoft.com/en-us/library/ee923636.aspx Accessed 2014/03/26].
[13]What you should know about Volume Shadow Copy/System Restore in Windows 7 & Vista (FAQ) .Available at: https://blog.szynalski.com/2009/11/23/volume-shadow-copy-system-restore/[Accessed 2014/03/27].
[14]Michael Raggo , Chet Hosmer (2013). Data Hiding: Exposing Concealed Data in Multimedia, Operating Systems, Mobile Devices and Network Protocols . Chapter 7. USA. Syngress.
About the author:
Nihad Hassan (Bachelor degree in Computer Science, Certified XML Master) is a freelancer computer security & forensic consultant and trainer with more than five years of experience in this domain. He has been working into the IT field since 2005 for both private and public sector, his main interest is developing websites based on .Net technology, database design & implementation, System analysis, in addition to his solid knowledge of XML & related technologies.
You can read more of his computer security tutorials at His blog www.darknessgate.com ,email him at [email protected] , twitter: https://twitter.com/darknessgate