No products in the cart.
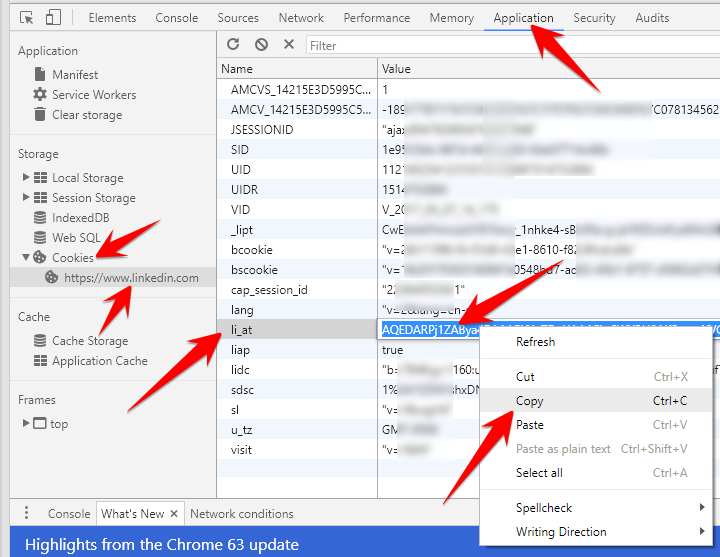
Scrapes any Linkedin data. Installation $ pip install git+git://github.com/jqueguiner/lk_scraper Setup Using Docker compose $ docker-compose up -d $ docker-compose run lk_scraper python3 Using Docker only for selenium server First, you need to run a selenium server $ docker run -d -p 4444:4444 --shm-size 2g selenium/standalone-firefox:3.141.59-20200326 After running this command, from the browser navigate to your IP address followed by the port number and /grid/console. So the command will be https://localhost:4444/grid/console. Retrieving Cookie Browser-Independent: Navigate to Linkedin.com and log in Open up the browser developer tools (Ctrl-Shift-I or right click -> inspect element) Chrome: Select the Application tab Under the Storage header on the left-hand menu, click the Cookies dropdown and select www.linkedin.com Find the li_at cookie, and double click the value to select it before copying Firefox: Select Storage tab Click the Cookies dropdown and select www.linkedin.com Find and copy the li_at value Setting up the cookie Method 1: Setting....
Subscribe
0 Comments