No products in the cart.
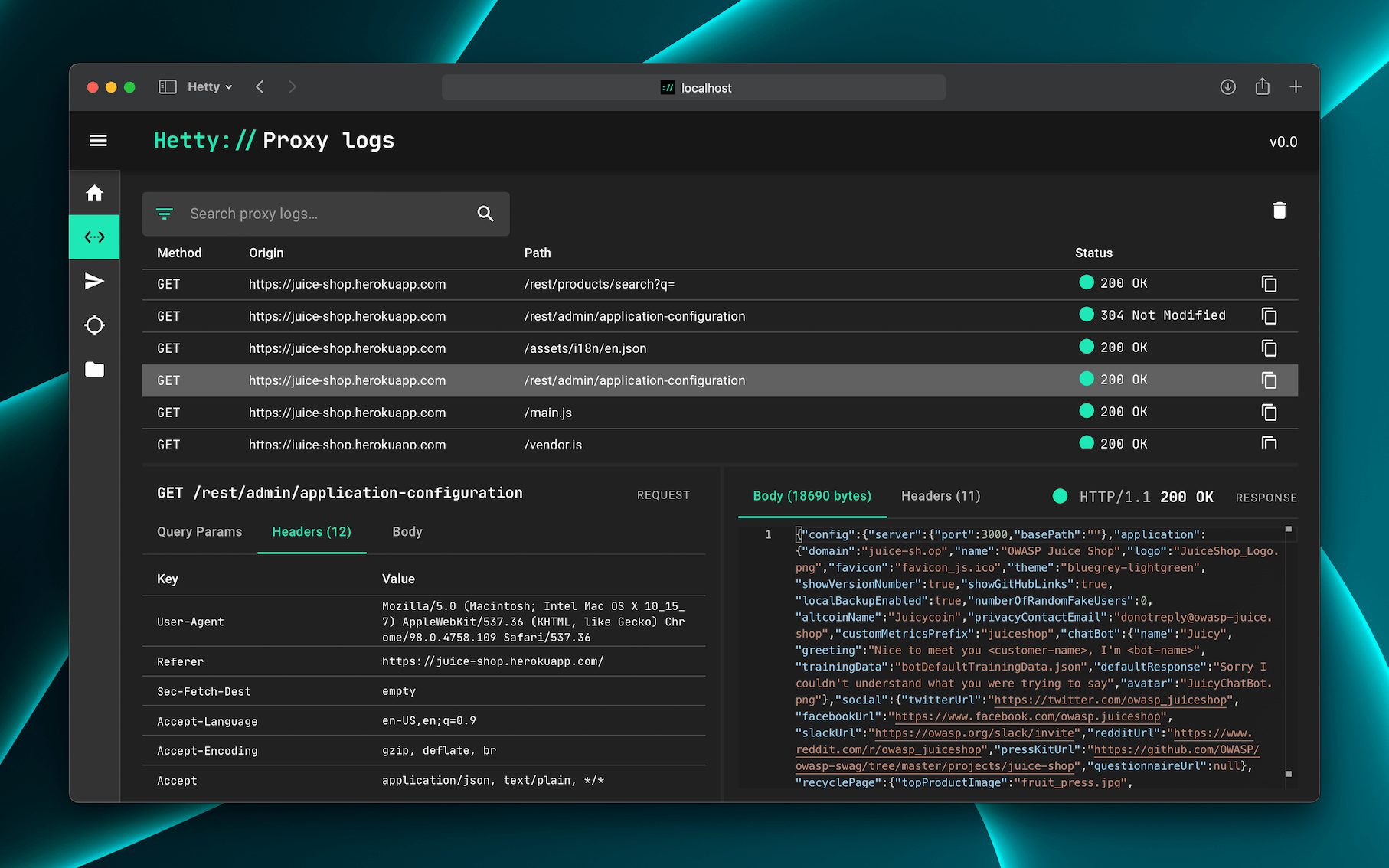
Hetty is an HTTP toolkit for security research. It aims to become an open source alternative to commercial software like Burp Suite Pro, with powerful features tailored to the needs of the infosec and bug bounty community. Features Machine-in-the-middle (MITM) HTTP proxy, with logs and advanced search HTTP client for manually creating/editing requests, and replay proxied requests Scope support, to help keep work organized Easy-to-use web based admin interface Project based database storage, to help keep work organized ℹ️ Hetty is in early development. Please see the backlog for details. Community ???? Join the Hetty Discord server. Documentation ???? Read the docs. Installation The quickest way to install and update Hetty is via a package manager: macOS brew install hettysoft/tap/hetty LINUX sudo snap install hetty WINDOWS scoop bucket add hettysoft https://github.com/hettysoft/scoop-bucket.git scoop install hettysoft/hetty Alternatively, you can download the latest release from GitHub for your OS and architecture, and move the....
A very big thanks to kelvinethicalhacker at gmail com for the great the work you done for me, i got the email address on the net web when i needed to hack my husband cell phone he helped me within few hours with whatsApp hacking and GPS location tracking direct from my person phone i know how my husband walks, thanks for the helped you do for me for every grateful for your helped, you can contact him through gmail via kelvinethicalhacker at gmail.com or Telegram, calls, text, number +1(341)465-4599, if you are in needed of hacking services, contact him..
A great hacker is really worthy of good recommendation , Henry
really help to get all the evidence i needed against my husband and
and i was able to confront him with this details from this great hacker
to get an amazing service done with the help ,he is good with what he does and the charges are affordable, I think all I owe him is publicity for a great work done via, Henryclarkethicalhacker at gmail com, and you can text, call him on whatsapp him on +12014305865, or +17736092741,