No products in the cart.
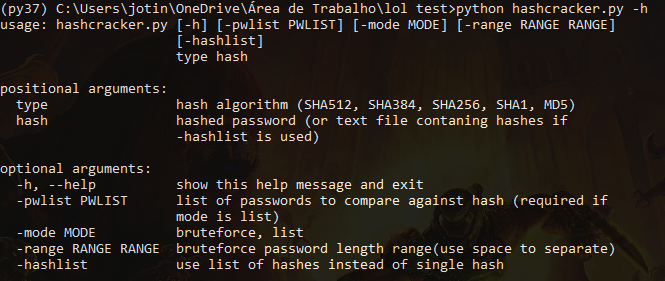
Supported hashing algorithms: SHA512, SHA256, SHA384, SHA1, MD5 Features: auto detection of hashing algorithm based on length (not recommended), bruteforce, password list Arguments: type: hash algorithm (must be one of the supported hashing algorithms mentioned above or AUTO if you want to use automatic algorithm detection) hash: can be either the hashed password, or a text file containing a list of hashes to crack (hashlist must be activated if hash is a text file containing multiple hashes) mode: list or bruteforce pwlist: list of passwords to compare against a single hash or a list of hashes range: bruteforce string length range (default: 8-11) hashlist: no parameters required for this argument, if hashlist is used, then hash should be a text file with more than 1 hash chars: string of characters to pick from to generate random strings for bruteforce (default value is: abcdefghijklmnopqrstuvwxyzABCDEFGHJIKLMNOPQRSTUVWXYZ0123456789) Examples: Cracking a single hash with a....
Subscribe
0 Comments