No products in the cart.
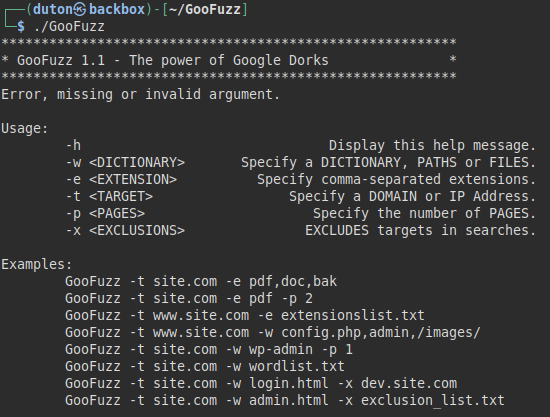
Credits Author: M3n0sD0n4ld Twitter: @David_Uton Description: GooFuzz is a script written in Bash Scripting that uses advanced Google search techniques to obtain sensitive information in files or directories without making requests to the web server. Download and install: $ git clone https://github.com/m3n0sd0n4ld/GooFuzz.git $ cd GooFuzz $ chmod +x GooFuzz $ ./GooFuzz -h Use: Menu Lists files by extensions separated by commas. Lists files by extensions contained in a txt file. Lists files by extension, either subdomain or domain and shows the first Google result. List files, directories, and even parameters by means of a wordlist (it is recommended to use only very small files). Lists directories and files by specifying paths, words, or file names. Exclusion of subdomains in your searches (separated by commas or by a list) Example 1: In this example, we remove the subdomain "mars.nasa.gov" from the search Example 2: We perform a normal file search by....
A very big thanks to kelvinethicalhacker at gmail com for the great the work you done for me, i got the email address on the net web when i needed to hack my husband cell phone he helped me within few hours with whatsApp hacking and GPS location tracking direct from my person phone i know how my husband walks, thanks for the helped you do for me for every grateful for your helped, you can contact him through gmail via kelvinethicalhacker at gmail.com or Telegram, calls, text, number +1(341)465-4599, if you are in needed of hacking services, contact him.
A great hacker is really worthy of good recommendation , Henry
really help to get all the evidence i needed against my husband and
and i was able to confront him with this details from this great hacker
to get an amazing service done with the help ,he is good with what he does and the charges are affordable, I think all I owe him is publicity for a great work done via, Henryclarkethicalhacker at gmail com, and you can text, call him on whatsapp him on +12014305865, or +17736092741,