No products in the cart.
IoT is a growing market and will be the future of our daily lives. Because of its emergence, there is no standard to guide the development process, there are many protocols and custom solutions to connect a hardware device to the cloud. This IoT course will explain IoT concepts, IoT construction, and security holes. Each student will train themselves on a dedicated open sourced vulnerable board. They will be able to improve their skills to find vulnerabilities and learn how to avoid them.
COURSE BENEFITS
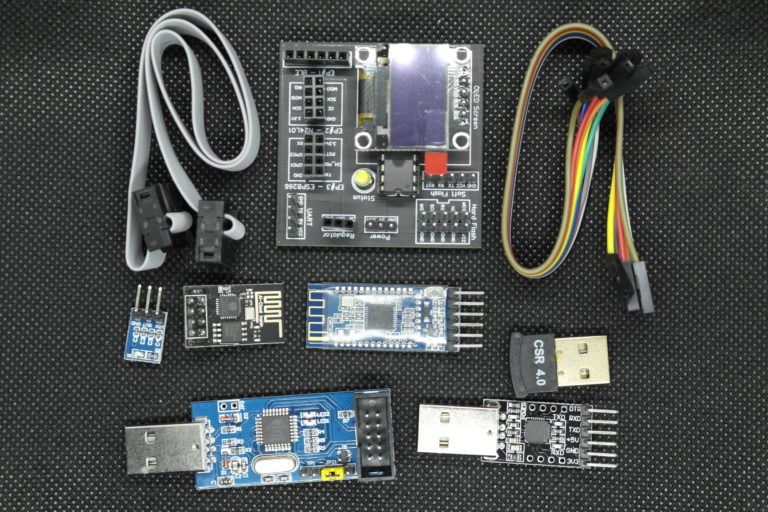
Each student will have the Damn Vulnerable IoT Device (DVID) with extension board (Bluetooth), a USBasp to flash the device, and USBuart to communicate with the board. For each training, the student will have to flash the corresponding firmware on the DVID board, to learn, hack, and find the challenge solution.
After completing the course, each student will be able to identify the most famous IoT vulnerabilities, plug his analysis tools into debug interfaces, analyze outgoing exchanges, understand protocols used, and do some fun tricks with them. They will also be able to write a relevant audit report with vulnerability details and remediation.
This course is based on the instructor's original research and his expertise in IoT Security. This course is designed to help:
- IoT makers, in order to help them develop with security guidelines and view impact about security absence
- Security researchers, in order to help them to identify the most famous vulnerabilities and be trained for them
- IT Decision makers, in order to help them have the correct reflexes when IoT knocks on their IT door
DURATION: 18 hours
CPE POINTS: On completion you get a certificate granting you 18 CPE points.
Course format:
- Self-paced
- Pre-recorded
- Accessible even after you finish the course
- No preset deadlines
- Materials are video, labs, and text
- All videos captioned
IMPORTANT NOTE
To fully participate in this course you need to have the DVID (Damn Vulnerable IoT Device). It is necessary to participate in the class. You can order one pre-made with this course, or manufacture one yourself - see instructions below.
BEFORE YOU START
The board is included in some course purchase options.
This IoT device is designed and manufactured by the course instructor. The main objective is to provide a vulnerable board to improve skills in IoT hacking. The board core is composed of an Atmega328p and an OLED screen. For each course challenge, a firmware is flashed on the Atmega328p in order to offer a specific vulnerable environment. There are also connection ports like UART, Bluetooth, 2,4Ghz and Wifi.
All community content is open sourced and published here: https://github.com/Vulcainreo/DVID
This board is necessary to participate in the "IoT Security - the DVID Challenge" online course. With some purchase options you'll get a pre-made, ready to go board.
The price includes international shipping, but it does not include any customs fees your country's Customs Office might charge. We are not responsible for getting your package through customs, and if your package is stopped at the border, you will be contacted by the Customs Office to make sure it goes through.
If you have the skills, you can purchase the standalone course (no DVID included), and using the open source schematic and component reference solder everything together. You are responsible for sourcing and financing all components and a naked board. The instructor can provide remote support throughout the process.
Premium subscriber? Order board only >>
Note about shipping
COVID-19: We are shipping normally. Due to restrictions, shipping time might be longer than usual, depending on the origin country. Please exercise all necessary caution when handling packages.
The packages will have tracking enabled, if they are shipped to the following countries: Germany, Saudi Arabia, Australia, Austria, Belgium, Brazil, Canada, South Korea, Croatia, Cyprus, Denmark, Spain, Estonia, United States, Finland, Gibraltar, Great Britain, Hong Kong, Hungary, Ireland, Iceland , Israel, Italy, Japan, Latvia, Lebanon, Lithuania, Luxembourg, Malaysia, Malta, Norway, New Zealand, Netherlands, Poland, Portugal, Russia, Singapore, Slovakia, Slovenia, Serbia, Sweden, Switzerland.
All packages going out to countries outside of this group will have tracking up to the point of arrival in the destination country.
As we have previously experienced issues with customs and delayed/lost packages when shipping to India, we will only be sending boards to India through a premium service (like DHL), which will include extra cost for you to cover.
- Basic knowledge of web and mobile security
- Knowledge of Linux OS
- Basic knowledge of programming - Python
- The DVID (either ordered pre-made here or made on your own; look below for details)
- Laptop with at least 50 GB free space
- 8+ GB minimum RAM (4+GB for the VM)
- External USB access (min. 2 USB ports)
- Administrative privileges on the system
- Virtualization software
Optional:
- Android phone
- Your favorite hacking tools (ex.: logic-analyzer)
The course will be organized as this table. The estimated duration is 18 hours with 7 hours of Practical Work, 11 hours of lectures. The course will finish with an at-home final exam.
Module 1 - Generalities
- Course time: 40 min
- Lab time estimation: 50 min
Module 2 - Hardware and firmware attacks
- Course time: 70 min
- Lab time estimation: 120 min
Module 3 - Middleware
- Course time: 140 min
- Lab time estimation: 280 min
Module 4 - Cloud
- Course time: 160 min
- Lab time estimation: 120 min
Module 5 - Reporting
- Course time: 100min
- Lab time estimation: N/A
Extra time should be alotted for the final exam. Your workload will depend on your skill level, but it will take at least a few hours to complete (no timers included).
About the author: Arnaud Courty
 As an IoT expert, my main mission is to evangelise companies to take care of security from the design step.
As an IoT expert, my main mission is to evangelise companies to take care of security from the design step.
I work on internal and external offensive security analysis and assessment of security maturity of embedded systems upstream of their industrialization.
Since the beginning of IoT, I specialize in vulnerabilities research adapted to the embedded systems but also awareness of designers, developers and integrators. I take advantage of security events and working groups to campaign for a less vulnerable IoT world.
Course Syllabus
Module 1: Generalities
This module will cover generalities about IoT. After a few reminders of protocols, we will discuss IoT architecture and discover the Practical Work board.
Understand most common IoT protocols
- UART
- JTAG
- SPI
- I2C
- CanBUS
- Zigbee
Discover the IoT Architecture and focus on Secbus architecture
- Security VS Safety
- Security Goals
- IoT product security life cycle
- SecBus architecture
- Discover what is an IoT object
- Discovering methodology
- Hardware identification
- Gain information on the Internet
- Make a schema
- Identify available attack
First steps with the DVID board
- Discover the Board
- Flash the first firmware
Start to dev an IoT Device
- IDE installation and configuration
- Code basics
- Compilation and flash
Module 2: Hardware and firmware attacks
This module will cover hardware and firmware attacks. After discovering all available attacks, we will discuss and train vulnerabilities on the DVID board.
Software:
- Discover what is a firmware (Definitions and Filesystem)
- How to extract sensitive information (Methodology and tools)
- Putting in a backdoor
Hardware:
Component identification.
- Recon
- Analysis (Static and dynamic)
Well known hardware attacks.
- Side channel attacks - Timing attacks
- Memory spying attacks
- On bus attacks
- Fault injections
Hardware reverse engineering.
Discover top 10 vulnerabilities with real-life examples.
 Datasheet exploration: The datasheet should help you to retrieve the information leak
Datasheet exploration: The datasheet should help you to retrieve the information leak
Firmware reverse: The root password was not provided in the manual, find it!
Vulnerability exploitation (hardcoded password) : A confidential message is stored on the firmware but protected by a password.
Vulnerability exploitation (default password): A confidential message is stored on the firmware but protected by a password. An informant said that the password was weak.
Module 3: Middleware interactions
This module will cover middleware interactions from hardware to cloud. After discovering a well known protocol, we will discuss and train about IoT usage and available attacks.
Discover middleware protocols
MQTT:
- Protocol explanation
- Play for fun
- PCAP reverse
Bluetooth:
- History
- Generic Access Profile (GAP)
- Profile, Services and Characteristics
- Pairing
- Ibeacons
CoAP:
- Protocol explanation
- CoRE link format
- Play for fun
Understand Android platform and security
- Overview
- Application architecture
- Application components
- Security
- Pentesting
Pentest methodology
- Middleware pentesting methodology
- TOP 10 OWASP on mobile devices
- Best practices
Advertising: a password is leaked from bluetooth advertising
Characteristics: interact with the board to exfiltrate flags
MQTT
Door locker analysis: Submit the correct password over MQTT to unlock it
Meetings: a meeting timetable and location are exchanged with MQTT, sniff the network to find them
Module 4: Cloud interaction
This module will cover cloud interaction from a device or device through a middleware. After discovering well known vulnerabilities, we will discuss and train about IoT specific vulnerabilities.
Cloud architecture
- Characteristics and model
- Architecture
- Related threats
Most common vulnerabilities
- Injection
- Weakness in authentication and session management
- Cross Site Scripting
- Weakness in access control
- Sensitive information exposure
- Weak protection against attacks
- Cross-Site Request Forgery (CSRF)
- Denial of service
Understanding API
- Definitions
- JSON Web Token (JWT)
Pentesting methodology
- Concepts
- Pentest Web methodology
- Information gathering
- Infrastructure analysis
- Application analysis
- Pentest API methodology
- CSRF: Find the CSRF vulnerability and force your victim to change their password
- SQLi: Find an SQL injection flaw to extract all stored password in order to crack them
- Cookie stealing: Exploit an XSS vulnerability to steal your victim's session cookies
Module 5: Audit methodology and reporting
This module will cover the audit methodology and reporting. We will discuss making relevant reports and as exhaustive as possible on vulnerabilities identification
Audit methodology overview
Analysis methodology
- Penetration planning
- Embedded device
- Network communication
- Server operating system
- Server application
Reporting methodology
Exam: Audit an IoT device
- EXAM INCLUDES CLOUD-HOSTED RESOURCES
- In this exam, students will be in front of an IoT device. This device could be controlled by an Android application.
- All learned skills about hardware analysis, middleware reverse or cloud exploration are needed to analyze the security of this IoT Device.
- Students must write a relevant report to show all findings and provide remediation on found vulnerabilities.
This exam will not have any time limit. Students have access to all slides and the Internet.
Marks:
- A flag is corresponding to vulnerability exploitation: 2 points per flag
- Making a relevant audit report: 8 points on report
- 10 bonus points for finding a 0-day :)
QUESTIONS?
If you have any questions, please contact our eLearning Manager at [email protected].
FAQ
ABOUT THE DVID:
The DVID (Damn Vulnerable IoT Device) is an intentionally vulnerable IoT device to help you learn about IoT security.
Yes. Without it you won’t be able to do any practical work throughout the course, a big part of the content will refer directly to it as well.
You can order a premade device with us, or you can make one yourself (buy all components and solder them together). For all instructions see the course description.
The DVID is manufactured by the instructor of the course, Arnaud Courty.
Yes. All boards are thoroughly tested before shipping, as well as all components and attack tools provided with the device.
No, we don’t offer part-only packages for retail customers. It is possible for group orders - see “Special orders” section.
SHIPPING:
Shipping will be done worldwide, but tracking will be available only for specific countries.
The packages will have tracking enabled, if they are shipped to the following countries: Germany, Saudi Arabia, Australia, Austria, Belgium, Brazil, Canada, South Korea, Croatia, Cyprus, Denmark, Spain, Estonia, United States, Finland, Gibraltar, Great Britain, Hong Kong, Hungary, Ireland, Iceland , Israel, Italy, Japan, Latvia, Lebanon, Lithuania, Luxembourg, Malaysia, Malta, Norway, New Zealand, Netherlands, Poland, Portugal, Russia, Singapore, Slovakia, Slovenia, Serbia, Sweden, Switzerland.
All packages going out to countries outside of this group will have tracking up to the point of arrival in the destination country.
We have previously experienced issues with customs and delayed/lost packages when shipping to India. For this reason, if you want to order the board, we will only be sending it through a premium service (like DHL), which will include extra cost for you to cover.
We will be contacting you by email with further instructions.
Since the boards are manufactured just for this course, we will contact you with specific details after you order. You will be notified when the shipment is made.
Please document the package and contact our e-Learning manager at [email protected]@hakin9.org
Please document the board and contact our e-Learning manager at [email protected]@hakin9.org
If you received a notice from us confirming that we’ve sent the package and the shipment does not arrive after a reasonable amount of time, please contact our e-Learning Manager at h9.courses@hakin9.org
I AM A HAKIN9 PREMIUM SUBSCRIBER / IT PACK PREMIUM SUBSCRIBER / LIFETIME SUBSCRIBER
Yes, the course is included in your subscription, but the board is not. Don’t worry, we have a special product made just for you, where you can purchase the pre-made board independently from the course: https://hakin9.org/product/board-only-dvid-challenge-w46/ You can also manufacture the board yourself, if you’re feeling up to it - see instructions in the course description.
No. The BOARD ONLY product includes only the pre-made board and course access is not included. You have course access through your premium subscription.
No, you should either purchase a seat on the course, or renew your subscription.
Yes, you will be able to view the training materials and see the assignments. However, you won’t be able to perform any practical exercises from the course, unless you make the board yourself (instructions provided in the course description).
SPECIAL ORDERS
My University would be interested in enrolling our students in this course. Are there any discounts?
Educational institutions receive a discount for course enrollment. The price of the DVIDs (if you choose to order them as well) will not be discounted. Please contact our Product Manager Marta Sienicka at [email protected] for further details.
You can make a bulk order, but the price will not be discounted - the price of the DVID as offered on the website includes bare manufacturing and shipping costs. Please contact our Product Manager Marta Sienicka at [email protected] for further details.
Yes, provided you meet certain criteria in regards to the amount of the packages you want. Please contact our Product Manager Marta Sienicka at [email protected] for further details.
Companies receive a discount for group course enrollment only. The price of the DVID (if you choose to order it as well) will not be discounted. Please contact our Product Manager Marta Sienicka at [email protected] for further details.
You can make a bulk order, but the price will not be discounted - the price of the DVID as offered on the website includes bare manufacturing and shipping costs. Please contact our Product Manager Marta Sienicka at [email protected] for further details.
Yes, provided you meet certain criteria in regards to the amount of complete packages you want. Please contact our Product Manager Marta Sienicka at [email protected] for further details.
RETURNS & REFUNDS
Please document the package and contact our e-Learning manager at h9.courses@hakin9.org. We offer replacements if you meet the criteria for one.
Please document the board and contact our e-Learning manager at h9.courses@hakin9.org. We offer replacements if you meet the criteria for one.
You can only return undamaged boards within 14 days of receiving them. You have to inform us of your intent to return within that time frame, by email at h9.courses@haking.org. You are responsible for the return shipment and its cost. It should be made to a return address we provide. You must provide us with proof of shipment within 7 days of informing us of intent to return. After we receive your return package, the board will be evaluated for damage, and if everything checks out, we’ll reverse your payment.
Yes. You can only return undamaged boards within 14 days of receiving them. You have to inform us of your intent to return within that time frame, by email at [email protected]. You are responsible for the return shipment and its cost. It should be made to a return address we provide. After we receive your return package, the board will be evaluated for damage, and if everything checks out, we’ll reverse your payment.
Yes, if you meet the criteria. For our return policy for online courses, please refer to our Terms of Service.
Yes, if you meet the criteria. For our return policy for online courses, please refer to our Terms of Service.
Course Reviews
No Reviews found for this course.