No products in the cart.
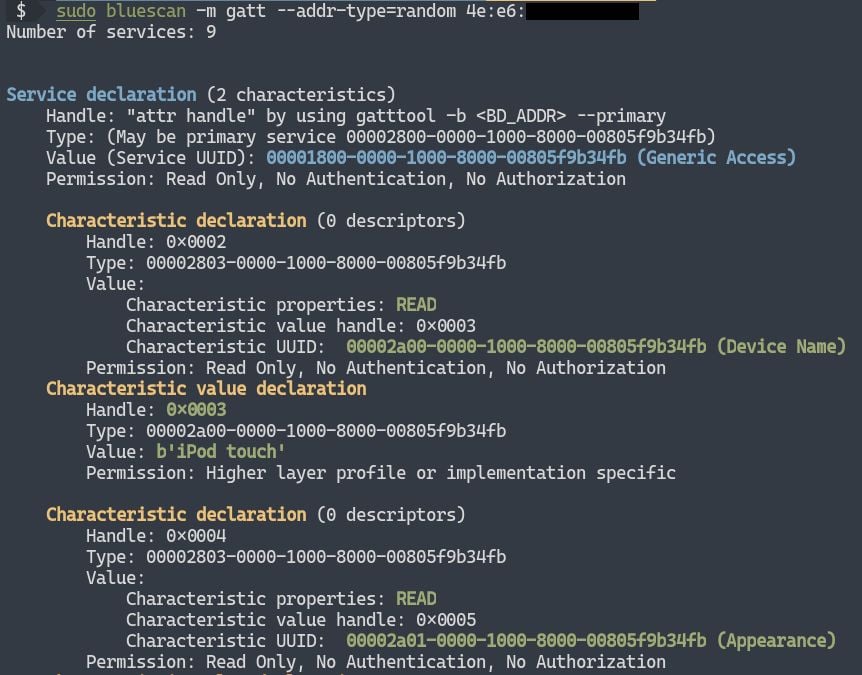
This project is maintained by Sourcell Xu from DBAPP Security HatLab. Bluetooth is a complex protocol, and a good scanner can quickly help us peek inside its secrets. But previous Bluetooth scanners suffered from a number of problems such as incomplete functionality, unintuitive information, and out-of repair. So we came up with this powerful Bluetooth scanner based on modern Python 3 ---- bluescan. When hacking Bluetooth targets, bluescan can be very useful for intelligence collecting. It can collect the following information: BR devices LE devices BR LMP features LE LL features SMP Pairing features Real-time advertising physical channel PDU SDP services GATT services Vulnerabilities (demo) Requirements bluescan is based on BlueZ, the official Linux Bluetooth stack. It only supports running on Linux, and the following packages need to be installed: sudo apt install python3-pip \ libcairo2-dev `# To solve the installation error "Failed to build pycairo" ` \ python3-dev `#....
Have you ever wanted to spy on your spouse’s phone or wanted to monitor their phone? you may want to know what is happening in their life or how they are communicating with someone else. or maybe you want to protect them from ex either way. you can contact ([email protected]), talk about it with kelvin. you want to hack your husband’s whatsapp account text messages on iphone or android phone remotely and provide ways of doing it without installing any software on the target device. you will get complete access to whatsapp, facebook, kik, viber, messenger, text messages and other… Read more »