No products in the cart.
Unveiling Cyber Threats: Understanding Reconnaissance in the Cyber Kill Chain and the importance of Threat Intelligence
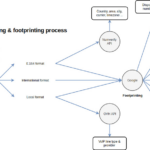
Introduction Many enterprises have significantly improved their cybersecurity posture the past decades, effectively preventing known attacks through the integration of …
Methods for Analyzing the Human Resource Aspect of Cybersecurity and Espionage
Introduction In the cybersecurity landscape, the concept of "watchers" encompasses a range of roles and intentions, each with its own …
Web Scraping Through Proxies: Why Your Business Needs It
In the digital age, data drives decisions, and web scraping is a key tool for businesses to harvest and analyze …

PhoneInfoga - Advanced information gathering & OSINT framework for phone numbers
PhoneInfoga is one of the most advanced tools to scan international phone numbers. It allows you to first gather standard …
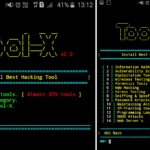
Tool-X is a Kali Linux hacking tools installer for Termux and linux system
Tool-X was developed for Termux and other android terminals. Using Tool-X, you can install almost 370+ hacking tools in Termux …
Beast Bomber - SMS bomber, email spammer, WhatsApp spammer, Telegram spammer, Discord spammer and DoS attacker.
Beast Bomber in Telegram: https://t.me/beast_bomberr_bot (in development) Beast Bomber in GitLab: https://gitlab.com/ebankoff/Beast_Bomber See also: https://github.com/ebankoff/CleanerPRO Possibilities SMS spammer(works better with …
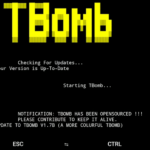
TBomb v2.1b An open-source SMS/call bomber for Linux And Termux.
NOTE: Due to the overuse of script, a bunch of APIs has been taken offline. It is okay if you …
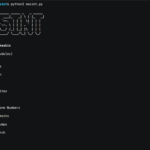
MOSINT - gather information about the target email
❓ What is MOSINT? MOSINT is an OSINT Tool for emails. It helps you gather information about the target email. …
hackingtool - All in One Hacking tool For Hackers
All in One Hacking tool For Hackers Your favorite tool is not in hackingtool or Suggestions Please CLICK HERE Update …
Python Cheat sheet for hackers and developers
This cheat sheet is about Python. It is one of the most used high-level programming languages. Most coders prefer using …
GHunt - Investigate Google Accounts with emails.
GHunt is a modulable OSINT tool designed to evolve over the years and incorporates many techniques to investigate Google accounts, …
Osintgram is a OSINT tool on Instagram
Disclaimer: FOR EDUCATIONAL PURPOSE ONLY! The contributors do not assume any responsibility for the use of this tool. Warning: It …
OpenCTI - Open Cyber Threat Intelligence Platform
OpenCTI is an open source platform allowing organizations to manage their cyber threat intelligence knowledge and observables. It has been …
PyPhisher - Easy to use phishing tool with 65 website templates
PyPhiser is an ultimate phishing tool in python. Includes popular websites like Facebook, Twitter, Instagram, Github, Reddit, Gmail, and many …
Car Hacking: The Ultimate Guide! - Part I by Anastasis Vasileiadis
Car safety is really exciting and is an interesting topic of study for many safety researchers. With the arrival of …
Live Forensicator - Powershell Script to aid Incidence Response and Live Forensics
___________ .__ __ \_ _____/__________ ____ ____ _____|__| ____ _____ _/ |_ ___________ | __)/ _ \_ __ \_/ __ …
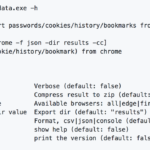
HackBrowserData - Decrypt passwords/cookies/history/bookmarks from the browser
HackBrowserData is an open-source tool that could help you decrypt data (password|bookmark|cookie|history|credit card|downloads link) from the browser. It supports the …
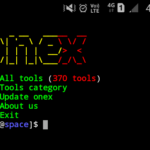
Onex - a Kali Linux hacking tools installer for Termux and other linux distribution.
"Onex a hacking tools library." Onex is a Kali Linux hacking tools installer for termux and other Linux distribution. It's …
Docker-OSX - Run Mac in a Docker container
Docker-OSX now has a Discord server & Telegram! The Discord is active on #docker-osx and anyone is welcome to come …
A.I.-driven shields design for cyber warriors.
Since more private data is stored and transmitted digitally, cybersecurity has emerged as a pressing concern in the Internet Age. …
Cyber Counter-Terrorism: Shutdown
Breaking through the vulnerabilities of fear From here, a perspective will be addressed regarding the power of information security as …
New frontiers, new worlds, new threats
Where are you going?There.What time will you be back?I will be back soon. Mr.Cardoso Image created in midjourney Introduction Since …
The process of developing tactics with the purpose of preparing for a cyberwar
Who are the cyber military powers today? Cyber military defenses are being developed by most of the developed countries in …

AWS Security Essentials: Building a Resilient Cloud Defense (W74)
"AWS Security Essentials: Building a Resilient Cloud Defense" is a concise course that provides essential knowledge and skills to secure your Amazon Web Services (AWS) cloud infrastructure effectively. Learn key security principles and best practices to safeguard your AWS resources and data against threats and vulnerabilities.
Create Your Own Command & Control Tool with Golang (W73)
Enter a short description of the course.
Kismet Wireless: Network Monitoring and Analysis (W72)
COURSE IS SELF-PACED, AVAILABLE ON DEMAND DURATION: 6 hours CPE POINTS: On completion, you get a certificate granting you 6 …