No products in the cart.
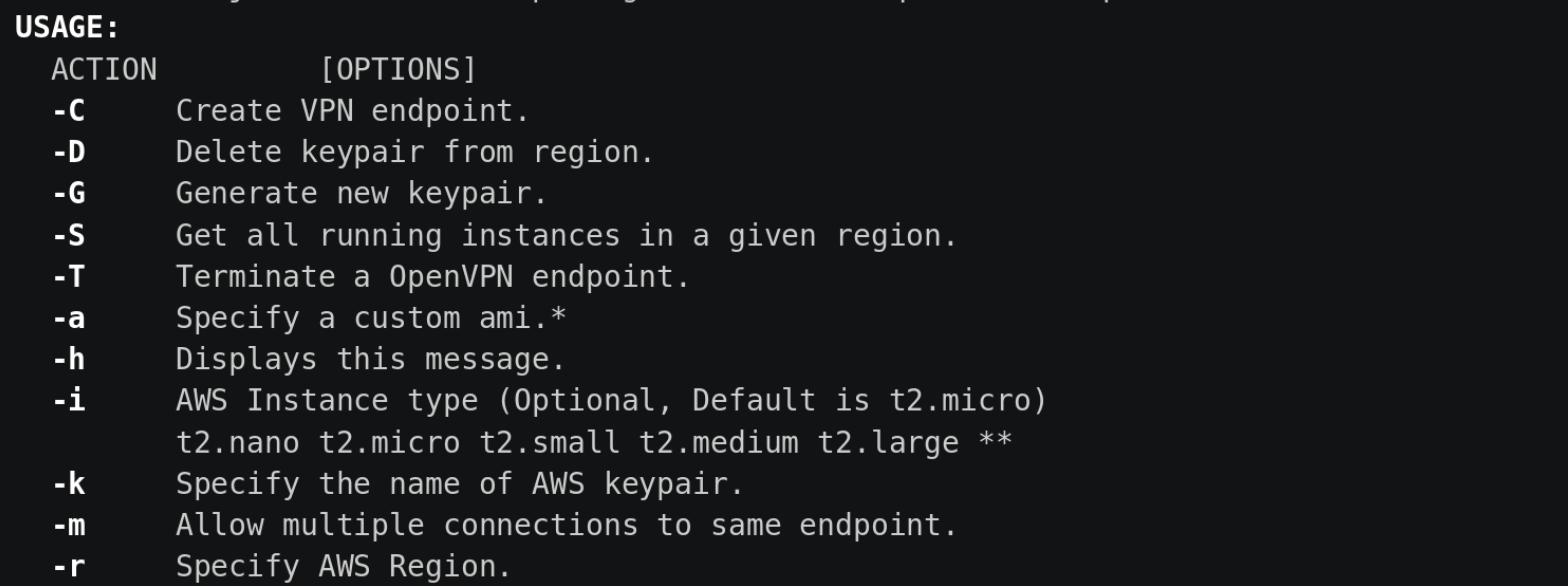
Autovpn is a script that allows the easy creation of OpenVPN endpoints in any AWS region. Creating a VPN endpoint is done with a single command that takes ~3 minutes. It will create the proper security groups. It spins up a tagged ec2 instance and configures OpenVPN software. Once the instance is configured an OpenVPN configuration file is downloaded and ready to use. There is also functionality to see which instances are running in which region and the ability to terminate the instance when done. Additional functionality includes specifying instance type, generate ssh keypairs, specify custom AMI, change login users, and more to come. Use Case Create on-demand OpenVPN Endpoints in AWS that can easily be destroyed after done only pay for what you use. Dependencies Create a virtualenv: mkvirtualenv -p python3 env/ source env/bin/activate Install dependencies by running pip install -r requirements.txt Ensure that you have an AWS .credentials....
Subscribe
0 Comments