No products in the cart.
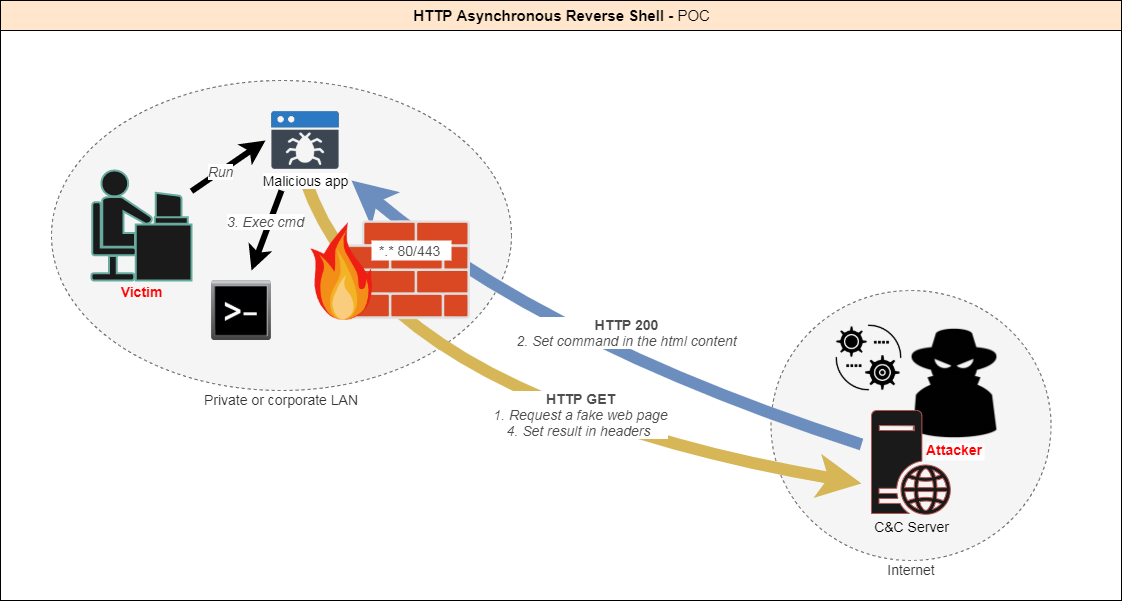
Today there are many ways to create a reverse shell in order to be able to remotely control a machine through a firewall. Indeed, outgoing connections are not always filtered. However, security software and hardware (IPS, IDS, Proxy, AV, EDR...) are more and more powerful and can detect these attacks. Most of the time the connection to a reverse shell is established through a TCP or UDP tunnel. I figured that the best way to stay undetected would be to make it look like legitimate traffic. The HTTP protocol is the most used by a standard user. Moreover, it is almost never filtered so as not to block access to websites. How does it work? The client app is executed on the target machine. The client initiates the connection with the server. The server accepts the connection. Then: -The client queries the server until it gets instructions. -The attacker provides....
so like basically you can just use the malicious payload & listener that metasploit provides instead of building your own payload and listener from scratch, that actual question was, to take advantage of the server with having to install a backdoor on their system!