No products in the cart.
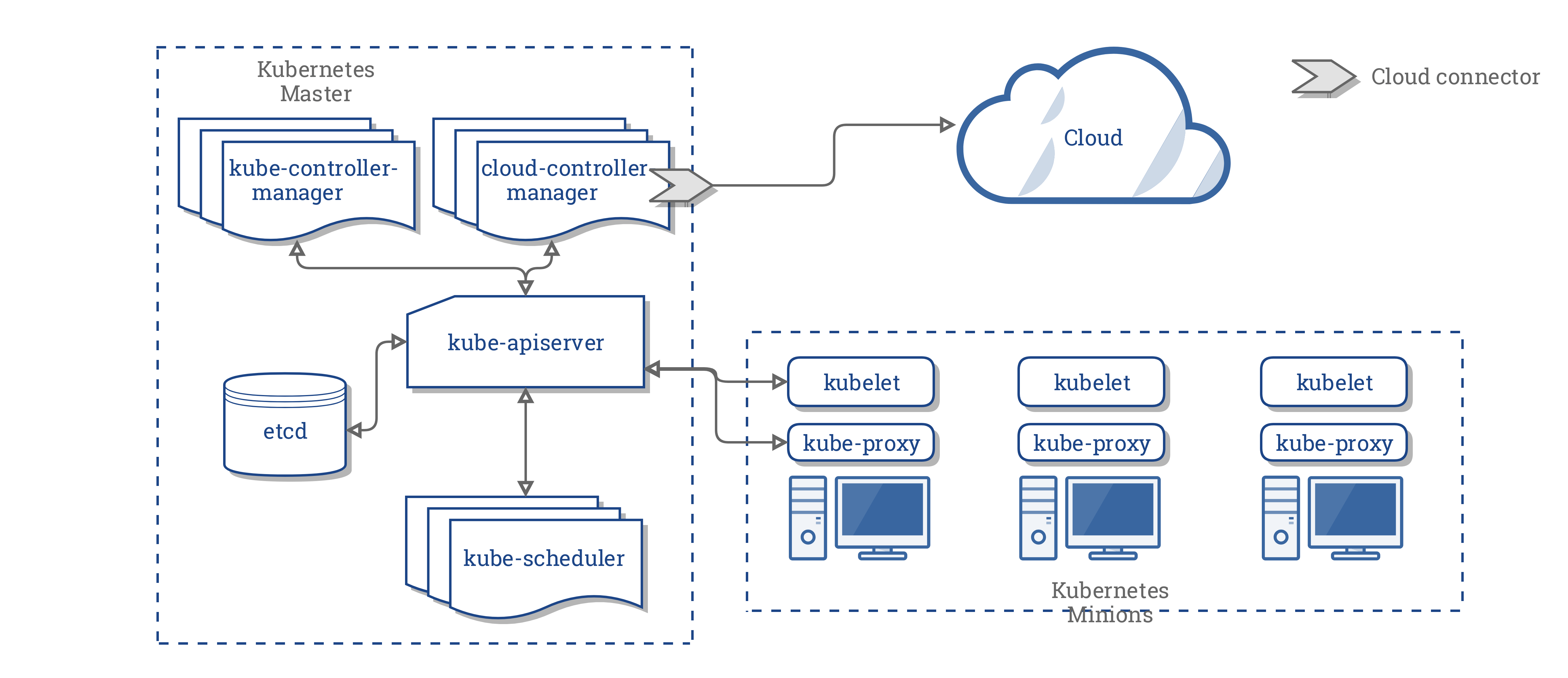
Unless you’ve been living under a rock for the past three years, you’ve probably heard about Kubernetes. At Handy, our infrastructure is backed by a multi-cluster Kubernetes ecosystem that drives our development, CI/CD, and production environments. You could say we are big advocates and users of Kubernetes at Handy, which is why we were both surprised and intrigued to learn that our coworker’s personal Kubernetes cluster was hacked this past weekend. We’re very glad it happened as it opened our eyes to a perhaps not so well known security “gotcha” in Kubernetes. In this article we will explore how our coworker’s cluster was hacked and how we recreated this attack in our own cluster as a proof of concept. This method of attack was tested in Kubernetes 1.9 but may also affect older clusters. DISCLAIMER: This article is regarding the compromise of a personal server owned by a coworker, not....
Subscribe
1 Comment
Newest