No products in the cart.
CryptoLocker Ransomware: The Crime That Can Be Prevented
by Dr. Rebecca Wynn
This week I received notification from a legal firm (after the fact) who had been infected with CryptoLocker Ransomware and all of their files where encrypted and held for ransom. Since they did not have backup shorter than a week their IT staff had recommend that they pay the ransom. They ended up having to pay $400 USD to get the files decrypted. They were lucky in that the criminals actually supplied the key and provided some technical assistance in retrieving the files. Goodson’s law firm in the North Carolina state capital Charlotte, had gone public on February 8, 2014 bravely admitting losing its entire cache of legal documents to the Cryptolocker Trojan despite attempting to pay the $300 ransom in a bid to have them unscrambled. (https://goo.gl/Doidpw) Right now, the FBI thinks international criminals are behind Cryptolocker. They’re investigating, but have not made any arrests just yet.
However, neither company would not have been in the vulnerable position in the first place if they had followed information security best business practices such as information security awareness training, thorough backup procedures, and group policy objects. It was a good lesson to learn but it to cost three days of productivity for one firm and undisclosed losses for another.
What is CryptoLocker?
CryptoLocker is a ransomware program that was released on the internet on September 5, 2013 that targets all versions of Windows including Windows XP, Windows Vista, Windows 7, and Windows 8.
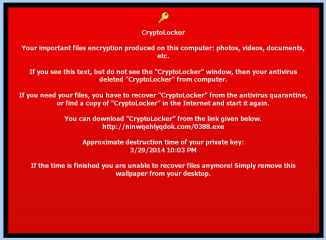
Figure 1. Payment
Early versions of CryptoLocker were distributed through spam emails targeting business professionals (as opposed to home Internet users). The lure was often a “consumer complaint” against the email recipient or their organization. Attached to these emails was a ZIP archive with a random alphabetical filename containing 13 to 17 characters. Only the first character of the filename is capitalized. The archive contained a single executable with the same filename as the ZIP archive but with an EXE extension.
This ransomware will encrypt certain files using a mixture of RSA & AES encryption. When it has finished encrypting your files, it will display a CryptoLocker payment program that prompts you to send a ransom of either $100 USD or $300 USD in order to decrypt the files. This screen will also display a timer stating that you have 72 hours or 4 days (typically as long as it takes to encrypt the detected data files), to pay the ransom or it will delete your encryption key and you will not have any way to decrypt your files. This ransom must be paid using MoneyPak vouchers or Bitcoins. Once you send the payment and it is verified, the program will decrypt the files that it encrypted.
Execution and Persistence
CryptoLocker hides its presence from victims until it has successfully contacted a command and control (C2) server and encrypted the files located on connected drives. Prior to these actions, the malware ensures that it remains running on infected systems and that it persists across reboots. When first executed, the malware creates a copy of itself in either %AppData% or %LocalAppData%. CryptoLocker then deletes the original executable file.
CryptoLocker then creates an “autorun” registry key:
HKCUSOFTWAREMicrosoftWindowsCurrentVersionRun “CryptoLocker”:<random>.exe
Some versions of CryptoLocker create an additional registry entry:
HKCUSOFTWAREMicrosoftWindowsCurrentVersionRunOnce “*CryptoLocker”:<random>.exe
The asterisk at the beginning of the key name ensures that the malware executes even if the system is restarted in “safe mode.”
Additional configuration data is stored in the following registry key:
HKCUSOFTWARECryptoLocker or HKCUSOFTWARECryptoLocker_0388
The VersionInfo value stored within this key contains configuration data encoded with the XOR key 0x819C33AE. The PublicKey value contains the RSA public key received from the C2 server during the initial network connection.
The executable files in early CryptoLocker samples used a random filename formatted like a GUID:
{71257279-042B-371D-A1D3-FBF8D2FADFFA}.exe
Network
The malware’s network communications use an internal domain generation algorithm (DGA) that produces 1,000 potential C2 domain addresses per day. The domain names contain 12 to 15 alphabetical characters and are within one of seven possible top-level domains (TLDs): com, net, org, info, biz, ru, and co.uk. An error in the algorithm prevents it from using ‘z’ in a generated domain name. The criminals never registered a domain under the ‘co.uk’ TLD, and Nominet, the official registrar for the ‘uk’ ccTLD, began to sinkhole all potential addresses under this domain on October 18, 2013. As a result, the criminals cannot use ‘co.uk’ domain names.
The criminals have also used static C2 servers embedded inside the malware. On October 17, 2013 a sample was distributed that first connected to inworkforallthen.com before cycling through the domains created by the DGA. Several days later, another sample was hard-coded to connect to ovenbdjnihhdlb.net prior to attempting other generated domains. Since that time, new samples frequently contain static addresses taken from the pool of domain names created by the DGA.
CryptoLocker cycles indefinitely until it connects to a C2 server via HTTP. After connecting to an attacker-controlled C2 server, CryptoLocker sends a phone-home message encrypted with an RSA public key embedded within the malware. Only servers with the corresponding RSA private key can decrypt this message and successfully communicate with an infected system.
CryptoLocker and Network Shares
CryptoLocker only encrypts data stored on network shares if the shared folders are mapped as a drive letter on the infected computer. Despite what some articles state, CryptoLocker does not encrypt data on a network through UNC shares. An example of a UNC share is \computernameopenshare.
It is strongly suggested that you secure all open shares by only allowing writable access to the necessary user groups or authenticated users. This is an important security principle that should be used at all times regardless of infections like CryptoLocker.
Encryption
Instead of using a custom cryptographic implementation like many other malware families, CryptoLocker uses strong third-party certified cryptography offered by Microsoft’s CryptoAPI. By using a sound implementation and following best practices, the malware authors have created a robust program that is difficult to circumvent. The malware uses the “Microsoft Enhanced RSA and AES Cryptographic Provider” (MS_ENH_RSA_AES_PROV) to create keys and to encrypt data with the RSA (CALG_RSA_KEYX) and AES (CALG_AES_256) algorithms.
The encryption process begins after CryptoLocker has established its presence on the system and successfully located, connected to, and communicated with an attacker-controlled C2 server. This communication provides the malware with the threat actors’ RSA public key, which is used throughout the encryption process.
The malware begins the encryption process by using the GetLogicalDrives() API call to enumerate the disks on the system that have been assigned a drive letter (e.g., C:). In early CryptoLocker samples, the GetDriveType() API call then determines if the drives are local fixed disks or network drives (DRIVE_FIXED and DRIVE_REMOTE, respectively). Only those two types of drives are selected for file encryption in early samples. Samples since late September also select removable drives (DRIVE_REMOVABLE), which can include USB thumb drives and external hard disks.
After selecting a list of disks to attack, the malware lists all files on those disks that match the 72 file patterns shown in Table 1. Over time, the criminals adjusted which types of files are selected for encryption; for example, PDF files were not encrypted in very early samples but were added in mid-September 2013. As a result, the list in the table below is subject to change.
Table 1. File patterns selected for encryption, which is growing
|
*.odt |
*.ods |
*.odp |
*.odm |
*.odb |
*.doc |
*.docx |
*.docm |
|
*.wps |
*.xls |
*.xlsx |
*.xlsm |
*.xlsb |
*.xlk |
*.ppt |
*.pptx |
|
*.pptm |
*.mdb |
*.accdb |
*.pst |
*.dwg |
*.dxf |
*.dxg |
*.wpd |
|
*.rtf |
*.wb2 |
*.mdf |
*.dbf |
*.psd |
*.pdd |
*.eps |
*.ai |
|
*.indd |
*.cdr |
????????.jpg |
????????.jpe |
img_*.jpg |
*.dng |
*.3fr |
*.arw |
|
*.srf |
*.sr2 |
*.bay |
*.crw |
*.cr2 |
*.dcr |
*.kdc |
*.erf |
|
*.mef |
*.mrw |
*.nef |
*.nrw |
*.orf |
*.raf |
*.raw |
*.rwl |
|
*.rw2 |
*.r3d |
*.ptx |
*.pef |
*.srw |
*.x3f |
*.der |
*.cer |
|
*.crt |
*.pem |
*.pfx |
*.p12 |
*.p7b |
*.p7c |
|
*.odc |
Each file is encrypted with a unique AES key, which in turn is encrypted with the RSA public key received from the C2 server. The encrypted key, a small amount of metadata, and the encrypted file contents are then written back to disk, replacing the original file. Encrypted files can only be recovered by obtaining the RSA private key held exclusively by the threat actors. As a form of bookkeeping, the malware stores the location of every encrypted file in the Files subkey of the HKCUSOFTWARECryptoLocker (or CryptoLocker_0388) registry key. After finishing the file encryption process, CryptoLocker periodically rescans the system for new drives and files to encrypt.
The malware does not reveal its presence to the victim until all targeted files have been encrypted.
The victim is presented with a splash screen containing instructions and an ominous countdown timer.
When You First Become Infected
When you first become infected with CryptoLocker, it will save itself as a random named filename to the root of the %AppData% or %LocalAppData% path. It will then create one of the following autostart entries in the registry to start CryptoLocker when you login:
KEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun “CryptoLocker”
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRunOnce “*CryptoLocker”
KEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun “CryptoLocker_<version_number>”
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRunOnce “*CryptoLocker_<version_number”
The infection will also hijack your .EXE extensions so that when you launch an executable it will attempt to delete the Shadow Volume Copies that are on the affected computer. It does this because you can use shadow volume copies to restore your encrypted files. The command that is run when you click on an executable is:
“C:WindowsSYsWOW64cmd.exe” /C “C:WindowsSysnativevssadmin.exe” Delete Shadows /All /Quiet
The .EXE hijack in the Registry will look similar to the following. Please note that registry key names will be random.
[HKEY_CLASSES_ROOT.exe]
@=”Myjiaabodehhltdr”
“Content Type”=”application/x-msdownload”
[HKEY_CLASSES_ROOT.exePersistentHandler]
@=”{098f2470-bae0-11cd-b579-08002b30bfeb}”
[HKEY_CLASSES_ROOTMyjiaabodehhltdr]
[HKEY_CLASSES_ROOTMyjiaabodehhltdrDefaultIcon]
@=”%1”
[HKEY_CLASSES_ROOTMyjiaabodehhltdrshell]
[HKEY_CLASSES_ROOTMyjiaabodehhltdrshellopen]
[HKEY_CLASSES_ROOTMyjiaabodehhltdrshellopencommand]
@=””C:\Users\User\AppData\Local\Rlatviomorjzlefba.exe” - ”%1” %*”
Once the infection has successfully deleted your shadow volume copies, it will restore your exe extensions back to the Windows defaults. As stated earlier, the infection will then attempt to find a live C2 server by connecting to domains generated by a DGA. Some examples of domain names that the DGA will generate are lcxgidtthdjje.org, kdavymybmdrew.biz, dhlfdoukwrhjc.co.uk, and xodeaxjmnxvpv.ru. Once a live C&C server is discovered it will communicate with it and receive a public encryption key that will be used to encrypt your data files. It will then store this key along with other information in values under the registry key under HKEY_CURRENT_USERSoftwareCryptoLocker_0388. Unfortunately, the private key that is used to decrypt the infected files is not saved on the computer but rather the Command & Control server.
Known File Paths and Registry Keys Used by CryptoLocker
This section lists all known file paths and registry keys used by CryptoLocker. The file paths and registry keys that are currently being used by CryptoLocker will be highlighted in blue.
The File paths that are currently and historically being used by CryptoLocker are:
%AppData%<random.exe> and %AppData%{<8 chars>-<4 chars>-<4 chars>-<4 chars>-<12 chars>}.exe
Examples of filenames using this path are: Rlatviomorjzlefba.exe and {34285B07-372F-121D-311F-030FAAD0CEF3}.exe.
In Windows XP, %AppData% corresponds to C:Documents and Settings<Login Name>Application Data.
In Windows Vista, 7, and 8, %AppData%C:Users<Login Name>AppDataRoaming.
%LocalAppData%<random.exe>
Examples of filenames using this path are: Rlatviomorjzlefba.exe.
In Windows XP, %LocalAppData% corresponds to C:Documents and Settings<Login Name>Local SettingsApplication Data.
In Windows Vista, 7, and 8, %LocalAppData% corresponds to C:Users<Login Name>AppDataLocal.
The Registry key that is used to automatically start CryptoLocker when you login to Windows are found below.
KEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun “CryptoLocker_<version_number>”
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRunOnce “*CryptoLocker_<version_number”
For the above registry values, the current version is 0388. Please note that the * in the RunOnce entry tells Windows to start CryptoLocker even in Windows Safe Mode.
CryptoLocker also creates a registry key to store its configuration information and the files that were encrypted. In the past the registry key that was used was HKEY_CURRENT_USERSoftwareCryptoLocker.
Newer version now include the version of the malware, which is currently 0388, in the key name.
The registry key that is currently being used to store the configuration information is HKEY_CURRENT_USERSoftwareCryptoLocker_0388. Under this key are 3 registry values that are described below:
|
Value Name |
Description |
|
PublicKey |
The PublicKey value contains the public key that was used to encrypt your files. This key will not help you decrypt the encrypted files on your computer. |
|
VersionInfo |
The VersionInfo value contains information that includes the current version of the malware, the IP address of the Command & Control server, and the timestamp of installation. |
|
Wallpaper |
The WallPaper value contains information regarding the wallpaper that will be shown as the background on the infected computer’s desktop. |
Under the HKEY_CURRENT_USERSoftwareCryptoLocker_0388Files key will be a list of all the files that have been encrypted by CryptoLocker. This list is then processed by the decryption tool to decrypt your files if you paid the ransom. For each file that is encrypted, a new REG_DWORD value will be created that is named using the full pathname to the encrypted file. When naming the values, CryptoLocker will replace all occurrences of the forward slash character (), with a question mark. An example of how an encrypted file’s value entry would be named is C:?Users?Public?Pictures?Sample Pictures?Penguins.jpg. You can use the ListCrilock program to export a human readable list of these encrypted files from the registry into a text file.
Note
Newer variants of CryptoLocker will attempt to delete all shadow copies when you first start any executable on your computer after becoming infected. Thankfully, the infection is not always able to remove the shadow copies, so you should continue to try restoring your files using this method.
Since the release of the CryptoLocker Decryption Service it is possible to decrypt files without this registry key being available. The new decrypter provided by this service will instead scan your files and attempt to decrypt them using the embedded private decryption key.
What Should You Do When You Discover Your Computer is Infected with CryptoLocker
When you discover that a computer is infected with CryptoLocker, the first thing you should do is disconnect it from your wireless or wired network. This will prevent it from further encrypting any files. Some people have reported that once the network connection is disconnected, it will display the CryptoLocker screen.
It is not advised that you remove the infection from the %AppData% folder until you decide if you want to pay the ransom. If you do not need to pay the ransom, simply delete the Registry values and files and the program will not load anymore. You can then restore your data via other methods.
It is important to note that the CryptoLocker infection spawns two processes of itself. If you only terminate one process, the other process will automatically launch the second one again. Instead use a program like Process Explorer (https://live.sysinternals.com/procexp.exe) and right click on the first process and select Kill Tree. This will terminate both at the same time.
Set the BIOS Clock Back
Cryptolocker has a payment timer that is generally set to 72 hours, after which time the price for your decryption key goes up significantly.
How to Find Files That Have Been Encrypted by CryptoLocker
There are currently three method that you can use to generate a list of files that have been possible encrypted. Each of these methods is outlined below.
Method 1: ListCriLock
If you wish to generate a list of files that have been encrypted, you can download the ListCriLock tool: https://download.bleepingcomputer.com/grinler/ListCrilock.exe.
When you run this tool it will generate a log file that contains a list of all encrypted files found under the HKCUSoftwareCryptoLockerFiles or the HKCUSoftwareCryptoLocker_0388Files key. Once it has completed it will automatically open this log in Notepad.
Method 2: Windows PowerShell
Another method is to use the Windows PowerShell:
For systems with PowerShell, you can dump the list of files in the CryptoLocker registry key using the following command:
(Get-Item HKCU:SoftwareCryptoLockerFiles).GetValueNames().Replace(“?”,””) | Out-File CryptoLockerFiles.txt -Encoding unicode
Make sure to include the “-Encoding unicode” parameter to ensure that filenames with Unicode characters are preserved.
Note
More recent variants seem to have changed their code to prevent the generation of such a list. It will be necessary to identify the corrupted files manually.
Method 3: Omnispear’s CryptoLocker Scan Tool
You can use the CryptoLocker Scan Tool (https://omnispear.com/tools/cryptolocker-scan-tool) from Omnispear to search for and list encrypted files found on your computer. This program will look for certain file identifiers that are normally found in a file based on that file’s extension. If the file identifier does not exist it would indicate that the file is either encrypted or corrupted.
Current Payment Options
Although early versions of CryptoLocker included numerous payment options, the criminals now only accept MoneyPak and Bitcoin. The Bitcoin option was originally marketed as the “most cheap option” for ransom payment based on the difference between the $300 USD ransom and the market rate of Bitcoins.
The variety of payment options and currency choices in early CryptoLocker versions suggests the criminals originally anticipated a global infection pattern. The criminals have elected to focus exclusively on English-speaking countries and removed the payment options less popular in these countries.
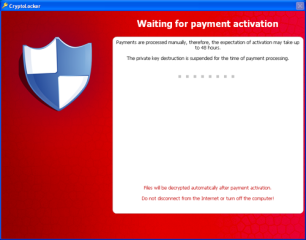
Figure 2. Ransom
Anecdotal reports from victims who elected to pay the ransom indicate that the CryptoLocker criminals honor payments by instructing infected computers to decrypt files and uninstall the malware. Victims who submit payments are presented with the payment activation screen shown below until the criminals validate the payment. During this payment validation phase, the malware connects to the C2 server every fifteen minutes to determine if the payment has been accepted. According to reports from victims, payments may be accepted within minutes or may take several weeks to process.
Collected Ransoms
In December 2013, Michele Spagnuolo published a thesis discussing a Bitcoin forensics framework called BitIodine (https://miki.it/articles/papers/#bitiodine). She discusses identifying Bitcoin addresses controlled by the CryptoLocker criminals and tracing potential ransom payments made to those addresses.
Using the daily weighted bitcoin currancy (BTC) price, if the criminals had collected and sold the estimated 1,216 total BTC collected over the period September-December 2013immediately upon receiving them, they would have earned nearly $380,000. If they elected to hold these ransoms, they would be worth nearly $599,488 as of this publication based on the current weighted price of $493/BTC (https://preev.com/). These figures represent a conservative estimate of the number of ransoms collected by the CryptoLocker criminals.
Mitigation
By incorporating the following components in a defense-in-depth strategy, organizations may be able to mitigate the CryptoLocker threat:
• Block executable files and compressed archives containing executable files before they reach a victim’s inbox. Email remains a top infection vector for malware in general and this threat in particular.
• Consider aggressively blocking known indicators (see Table 6) from communicating with your network to temporarily neuter the malware until it can be discovered and removed. CryptoLocker does not encrypt files until it has successfully contacted an active C2 server.
• Reevaluate permissions on shared network drives to prevent unprivileged users from modifying files.
• Regularly back up data with so-called “cold,” offline backup media. Backups to locally connected, network-attached, or cloud-based storage are not sufficient because CryptoLocker encrypts these files in the same manner as those found on the system drive.
• Implement Software Restriction Policies (SRPs) to prevent programs like CryptoLocker from executing in common directories such as %AppData% or %LocalAppData%.
• Use Group Policy Objects (GPOs) to create and restrict permissions on registry keys used by CryptoLocker, such as HKCUSOFTWARECryptoLocker (and variants). If the malware cannot open and write to these keys, it terminates before encrypting any files.
Below are a few Path Rules that are recommended not only block the infections from running, but also to block attachments from being executed when opened in an e-mail client.
Block CryptoLocker executable in %AppData%
Path: %AppData%*.exe
Security Level: Disallowed
Description: Don’t allow executables to run from %AppData%.
Block CryptoLocker executable in %LocalAppData%
Path if using Windows XP: %UserProfile%Local Settings*.exe
Path if using Windows Vista/7/8: %LocalAppData%*.exe
Security Level: Disallowed
Description: Don’t allow executables to run from %AppData%.
Block Zbot executable in %AppData%
Path: %AppData%**.exe
Security Level: Disallowed
Description: Don’t allow executables to run from immediate subfolders of %AppData%.
Block Zbot executable in %LocalAppData%
Path if using Windows XP: %UserProfile%Local Settings**.exe
Path if using Windows Vista/7/8: %LocalAppData%**.exe
Security Level: Disallowed
Description: Don’t allow executables to run from immediate subfolders of %AppData%.
Block executables run from archive attachments opened with WinRAR:
Path if using Windows XP: %UserProfile%Local SettingsTempRar**.exe
Path if using Windows Vista/7/8: %LocalAppData%TempRar**.exe
Security Level: Disallowed
Description: Block executables run from archive attachments opened with WinRAR.
Block executables run from archive attachments opened with 7zip:
Path if using Windows XP: %UserProfile%Local SettingsTemp7z**.exe
Path if using Windows Vista/7/8: %LocalAppData%Temp7z**.exe
Security Level: Disallowed
Description: Block executables run from archive attachments opened with 7zip.
Block executables run from archive attachments opened with WinZip:
Path if using Windows XP: %UserProfile%Local SettingsTempwz**.exe
Path if using Windows Vista/7/8: %LocalAppData%Tempwz**.exe
Security Level: Disallowed
Description: Block executables run from archive attachments opened with WinZip.
Block executables run from archive attachments opened using Windows built-in Zip support:
Path if using Windows XP: %UserProfile%Local SettingsTemp*.zip*.exe
Path if using Windows Vista/7/8: %LocalAppData%Temp*.zip*.exe
Security Level: Disallowed
Description: Block executables run from archive attachments opened using Windows built-in Zip support.
Cryptolocker 2.0
This infection appears to be a copycat trying to benefit from the fame of the original infection (https://www.welivesecurity.com/2013/12/19/cryptolocker-2-0-new-version-or-copycat/).
The main differences between the two are:
• A major indication that this is a copycat is that it is programmed using a completely different language. The original is programmed in native C++ code that did not have any prerequisites to execute on a computer. CryptoLocker 2.0 is written in C# that requires the .NET Framework 4.0 to run.
• This malware contains a cryptocoin miner called BFGMiner that could allow it to mine Bitcoins, and other crypto coins, using the CPU power or graphic card on your computer. The mined coins would then go into the wallet of the malware developer.
• Based on strings found in the executable, this malware appears to be able perform DDOS attacks.
• The malware does not use a domain generation algorithm, but instead hard codes the C2 server’s address.
• Uses a different encryption type then the original CryptoLocker
When installed, the dropper will install the main executable as:
%AppData%Microsoftmsunet.exe
It will then create the following registry keys to autostart the program in normal mode and safe mode.
HKCUSoftwareMicrosoftWindowsCurrentVersionRunMSUpdate %AppData%Microsoftmsunet.exe
HKCUSoftwareMicrosoftWindowsCurrentVersionRunOnce*MSUpdate %AppData%Microsoftmsunet.exe
HKCUSoftwareMicrosoftWindows NTCurrentVersionWinlogonUserinit C:Windowssystem32userinit.exe,,%AppData%Microsoftmsunet.exe
The infection encrypts files with the following extensions;
3fr, accdb, txt, ai, arw, bay, cdr, cer, cr2, eps, erf, indd, mp3, mp4, jpe, jpg, kdc, mdb, mdf, mef, mrw, nef, crt, crw, dbf, dcr, der, dng, doc, docm, docx, dwg, dxf, dxg, rwl, srf, srw, wb2, wpd, wps, xlk, nrw, odb, odm, odp, ods, odt, orf, p12, p7b, p7c, pdd, xls, xlsb, xlsm, xlsx, pef, pem, pfx, ppt, pptm, pptx, psd, pst, ptx, r3d, raf, raw, rtf
Over all, the developer of this malware drastically changed the approach of the original CryptoLocker. Instead of focusing on encrypting files and getting paid for the decryption key, this infection tries to throw the kitchen sink at you in order to maximize revenue.
Conclusion
Mine, the FBI the UK’s National Crime Agency and many others advice is to not to give in to crooks by paying this ransom.
Paying the criminals may get your data back, but there have been plenty of cases where the decryption key never arrived or where it failed to properly decrypt the files. Ransoming anything is not a legitimate business practice, and the malware authors are under no obligation to do as promised. They can take your money and provide nothing in return, because there is no backlash if the criminals fail to deliver.
The only reason this type of attack succeeds is because people are willing to pay up. If no-one ever paid, there would be no ransomware.
Protect your systems now my best business practices such as:
Back up your data
The greatest factor that will defeat ransomware is having a regularly updated backup. If you are attacked with ransomware you may lose that document you started earlier this morning, but if you can restore your system to an earlier snapshot or clean up your machine and restore your other lost documents from backup, you can rest easy. Remember that Cryptolocker will also encrypt files on drives that are mapped. This includes any external drives such as a USB thumb drive, as well as any network or cloud file stores that you have assigned a drive letter. So, what you need is a regular backup regimen, to an external drive or backup service, one that is not assigned a drive letter or is disconnected when it is not doing backup.
• Purchase an external USB 2.0 hard drive for your backups. It’s a worthwhile investment that pays for itself with one system recovery. Dedicate the drive to backup; don’t use it for anything else.
• Schedule a full-system backup once a week and smaller, incremental backups (that store only changes to files) daily or nightly.
Show hidden file-extensions
One way that Cryptolocker frequently arrives is in a file that is named with the extension “.PDF.EXE”, counting on Window’s default behavior of hiding known file-extensions. If you re-enable the ability to see the full file-extension, it can be easier to spot suspicious files.
Filter EXEs in email
If your gateway mail scanner has the ability to filter files by extension, you may wish to deny mails sent with “.EXE” files, or to deny mails sent with files that have two file extensions, the last one being executable (“*.*.EXE” files, in filter-speak). If you do legitimately need to exchange executable files within your environment and are denying emails with “.EXE” files, you can do so with ZIP files (password-protected, of course) or via cloud services.
Disable files running from AppData/LocalAppData folders
You can create rules within Windows or with Intrusion Prevention Software, to disallow a particular, notable behavior used by Cryptolocker, which is to run its executable from the App Data or Local App Data folders. If (for some reason) you have legitimate software that you know is set to run not from the usual Program Files area but the App Data area, you will need to exclude it from this rule.
Disable RDP if not required
The Cryptolocker/Filecoder malware often accesses target machines using Remote Desktop Protocol (RDP), a Windows utility that allows others to access your desktop remotely. If you do not require the use of RDP, you can disable RDP to protect your machine from Filecoder and other RDP exploits.
Patch or Update your software
Make a practice of updating your software often. Some vendors release security updates on a regular basis (Microsoft and Adobe both use the second Tuesday of the month), but there are often “out-of-band” or unscheduled updates in case of emergency. Enable automatic updates if you can for anti-virus/anti-malware.
Use a reputable security suite
Have both anti-malware software and a software firewall to help you identify threats or suspicious behavior.
If infected, disconnect from WiFi or unplug from the network immediately
If you run a file that you suspect may be ransomware, but you have not yet seen the characteristic ransomware screen, if you act very quickly you might be able to stop communication with the C&C server before it finish encrypting your files. If you disconnect yourself from the network immediately, you might mitigate the damage. It takes some time to encrypt all your files, so you may be able to stop it before it succeeds in garbling them all. This technique is definitely not foolproof, and you might not be sufficiently lucky or be able to move more quickly than the malware, but disconnecting from the network may be better than doing nothing.
Use System Restore to get back to a known-clean state
If you have System Restore enabled on your Windows machine, you might be able to take your system back to a known-clean state. But, again, you have to out-smart the malware. Newer versions of Cryptolocker can have the ability to delete “Shadow” files from System Restore, which means those files will not be there when you try to replace your malware-damaged versions. Cryptolocker will start the deletion process whenever an executable file is run, so you will need to move very quickly as executables may be started as part of an automated process. That is to say, executable files may be run without you knowing, as a normal part of your Windows system’s operation.
Set the BIOS clock back
Cryptolocker has a payment timer that is generally set to 72 hours, after which time the price for your decryption key goes up significantly. You can “beat the clock” somewhat, by setting the BIOS clock back to a time before the 72 hour window is up.
Lastly
A word of thanks to the person who developed CryptoLocker. I am a security enthusiast and people don’t always believe my passion until a creative genius like yourself brings them a nightmare. I would encourage you to use your skills to bring peace to the world instead of distress.
References
• https://www.welivesecurity.com/2013/12/19/cryptolocker-2-0-new-version-or-copycat/
• https://www.bleepingcomputer.com/virus-removal/cryptolocker-ransomware-information
• https://nakedsecurity.sophos.com/2014/03/07/1-in-30-have-been-hit-by-cryptolocker-and-40-pay-the-ransom-says-study/
• https://www.secureworks.com/cyber-threat-intelligence/threats/cryptolocker-ransomware/
• https://miki.it/articles/papers/#bitiodine
• https://www.symantec.com/connect/articles/recovering-ransomlocked-files-using-built-windows-tools
• https://www.symantec.com/docs/TECH211589
• https://www-secure.symantec.com/connect/blogs/ransomcrypt-thriving-menace
• https://omnispear.com/tools/cryptolocker-scan-tool
• https://www.welivesecurity.com/2013/12/12/11-things-you-can-do-to-protect-against-ransomware-including-cryptolocker/
• https://en.wikipedia.org/wiki/Domain_generation_algorithm
• https://www.welivesecurity.com/2013/12/19/cryptolocker-2-0-new-version-or-copycat/
• https://www.fbi.gov/washingtondc/news-and-outreach/stories/cryptolocker-ransomware-encrypts-users-files
• https://www.nationalcrimeagency.gov.uk/news/256-alert-mass-spamming-event-targeting-uk-computer-users
About the Author
Dr. Rebecca Wynn, DHL, MBA, CISSP, CASP, CRISC, CCISO, LPT, ECSA, CEH, CIWSA, CIWSP, CCSK, CWNA, GSEC, MCP, MCTS SQL Server 2005, Security+, Security+ CE, Project+, ITILv3, NSA/CNSS NSTISSI 4011-4016 is a Lead/ Senior Principal Security Engineer with NCI Information Systems, Inc. She has been on the Editorial Advisory Board and Contributor for Hakin9 Practical Protection IT Security Magazine since 2008 and is a regular contributor for Hakin9, PenTest, and Enterprise IT Security magazines, She is a Privacy by Design Ambassador under the Information & Privacy Commissioner for Ontario, Canada (www. privacybydesign.ca).
September 2, 2014
- AES
- Bitcoin
- BTC
- C2 server
- CASP
- CCISO
- CCSK
- CEH
- cissp
- CIWSA
- CIWSP
- CRISC
- CryptoLocker
- CryptoLocker Decryption Service
- CWNA
- DHL
- ECSA
- FBI
- GSEC
- HTTP
- ITILv3
- L|PT
- malware
- MBA
- MCP
- MCTS SQL Server 2005
- MoneyPak
- National Crime Agency
- NSA/CNSS NSTISSI 4011-4016
- PowerShell
- private key
- Project+
- PublicKey
- ransomware
- RSA
- RSA private key
- RSA public key
- RunOnce
- Scan Tool
- Security
- Security+ CE
- Software Restriction Policies
- SRPs
- timestamp
- VersionInfo
- windows
- Windows Safe Mode